AD FS SSO Integration Guide - PagerDuty
Maybe your like
Products
Angle Right IconProducts
Angle Right IconIncident Management
End-to-end orchestration for rapid issue resolution.
AI at PagerDuty
Revolutionize operations at the speed of AI.
Automation
Accelerate critical work across the enterprise.
AI Agents
Redefine operations with AI Agents that ignite growth.
Status Pages
A single source of truth for system status.
PagerDuty Advance
Generative AI for critical operations work.
Customer Service Ops
Bridge support and engineering teams.
AIOps
Reduce alert noise and accelerate triage.
Platform
Angle Right IconDeveloper Platform
Customize your PagerDuty experience.
Professional Services
Get more value from PagerDuty.
Security
View our trust and compliance practices.
Enterprise Class
Secure, reliable, extensible, and scalable.
Integrations
Work how you want with PagerDuty.
Featured PagerDuty Template and Prompt LibraryDiscover what PagerDuty Automation can do for you.
Explore now Featured PagerDuty Template and Prompt LibraryDiscover what PagerDuty Automation can do for you.
Explore nowSolutions
Angle Right IconSolutions
Angle Right IconIncident Management Transformation
Operations Center Modernization
Automation Standardization
Customer Experience Operations
Digital Operations Resiliency
Scaled Service Ownership
Remote-Location Operations
Use Cases
Angle Right IconSecurity Incident Management
LLMOps
DataOps
FinOps
ComplianceOps
CrisisOps
See All Use Cases →
Industries
Angle Right IconFinancial Services
Healthcare
Non Profit
Government
Education
Retail
AI Infrastructure
Featured Operational Integrity at FOX
Operational Integrity at FOX Learn how strategic technology investments powered FOX's digital and operational transformation.
Watch nowWork how you want with PagerDuty.
Explore our 700+ integrations Explore our 700+ integrations Featured Operational Integrity at FOX
Operational Integrity at FOX Learn how strategic technology investments powered FOX's digital and operational transformation.
Watch nowPricing
Company
Angle Right IconWho We Are
Angle Right IconThought Leadership
Awards
Careers
Investor Relations
Leadership
Newsroom
About us
We're empowering teams with the time and efficiency to build the future.
Learn moreOur Impact
See how we are building resilience and accelerating change.
Learn more Featured FY25 Impact Report
FY25 Impact Report Learn about our efforts around global employee engagement, sustainability, and more.
Read the report Featured FY25 Impact Report
FY25 Impact Report Learn about our efforts around global employee engagement, sustainability, and more.
Read the reportResources
Angle Right IconResources
Angle Right IconLibrary
Blog
Demos
Webinars
Events
Ebooks
Customer Stories
Angle Right IconTUI
Zoom
Spotify
DraftKings
Australian Bank
Vodafone
Fox Corporation
See All Customers →
Learning
Angle Right IconTemplate and Prompt Library
PagerDuty University
Community
Ops Guides
Knowledge Base
Featured PagerDuty on Tour - On Demand
PagerDuty on Tour - On Demand Get leading-edge insights from our leadership and customers at PagerDuty on Tour
Watch NowHave a question? We're here to help.
Contact Us Contact Us Featured PagerDuty on Tour - On Demand
PagerDuty on Tour - On Demand Get leading-edge insights from our leadership and customers at PagerDuty on Tour
Watch NowProducts
Platform
PagerDuty Operations CloudThe platform for mission-critical work in the modern enterprise.
Incident ManagementEnd-to-end orchestration for rapid issue resolution.
AI at PagerDutyRevolutionize operations at the speed of AI.
AutomationAccelerate critical work across the enterprise.
AI AgentsRedefine operations with AI Agents that ignite growth.
Status PagesA single source of truth for system status.
PagerDuty AdvanceGenerative AI for critical operations work.
Customer Service OpsBridge support and engineering teams.
AIOpsReduce alert noise and accelerate triage.
Work how you want with PagerDuty.
Explore our 700+ integrations Developer PlatformCustomize your PagerDuty experience.
Professional ServicesGet more value from PagerDuty.
SecurityView our trust and compliance practices.
Enterprise ClassSecure, reliable, extensible, and scalable.
IntegrationsWork how you want with PagerDuty.
See how PagerDuty works for you.
Request a demo New! PagerDuty Template and Prompt LibraryDiscover what PagerDuty Automation can do for you.
Explore nowSolutions
Incident Management Transformation Operations Center Modernization Automation Standardization Customer Experience Operations Digital Operations Resiliency Scaled Service Ownership Remote-Location OperationsUse Cases
Security Incident Management LLMOps DataOps FinOps ComplianceOps CrisisOps See All Use Cases →Industries
Financial Services Healthcare Non Profit Government Education Retail AI Infrastructure Featured Operational Integrity at FOX
Operational Integrity at FOX Learn how strategic technology investments powered FOX's digital and operational transformation.
Watch nowWork how you want with PagerDuty.
Explore our 700+ integrationsWho We Are
Thought Leadership Awards Careers Investor Relations Leadership NewsroomAbout us
We're empowering teams with the time and efficiency to build the future.
Learn moreOur Impact
See how we are building resilience and accelerating change.
Learn more Featured FY25 Impact Report
FY25 Impact Report Learn about our efforts around global employee engagement, sustainability, and more.
Read the reportResources
Library Blog Demos Webinars Events EbooksCustomer Stories
TUI Zoom Spotify DraftKings Australian Bank Vodafone Fox Corporation See All Customers →Learning
Template and Prompt Library PagerDuty University Community Ops Guides Knowledge Base Featured PagerDuty on Tour - On Demand
PagerDuty on Tour - On Demand Get leading-edge insights from our leadership and customers at PagerDuty on Tour
Watch NowHave a question? We're here to help.
Contact Us- PagerDuty /
- Integrations /
- AD FS SSO Integration Guide
Active Directory Federation Services (AD FS) is a technology that extends your Active Directory configuration to services outside of your infrastructure. With AD FS, you can give users access to PagerDuty without them having to manage another set of credentials.
This guide was written and tested on Windows Server 2012 R2 (also tested with Windows Server 2016), however earlier versions of Windows Server provide AD FS as well.
Note
You must be the Account Owner of your PagerDuty account in order to make these changes. Additionally, SSO capabilities within PagerDuty are only available on our Professional, Business and Digital Operations plans. Please contact our sales team if you are interested in upgrading your plan.
On Your AD FS Server
- Open the AD FS Management console, click Add Relying Party Trust... in the Actions pane and click Start on the wizard introduction page.
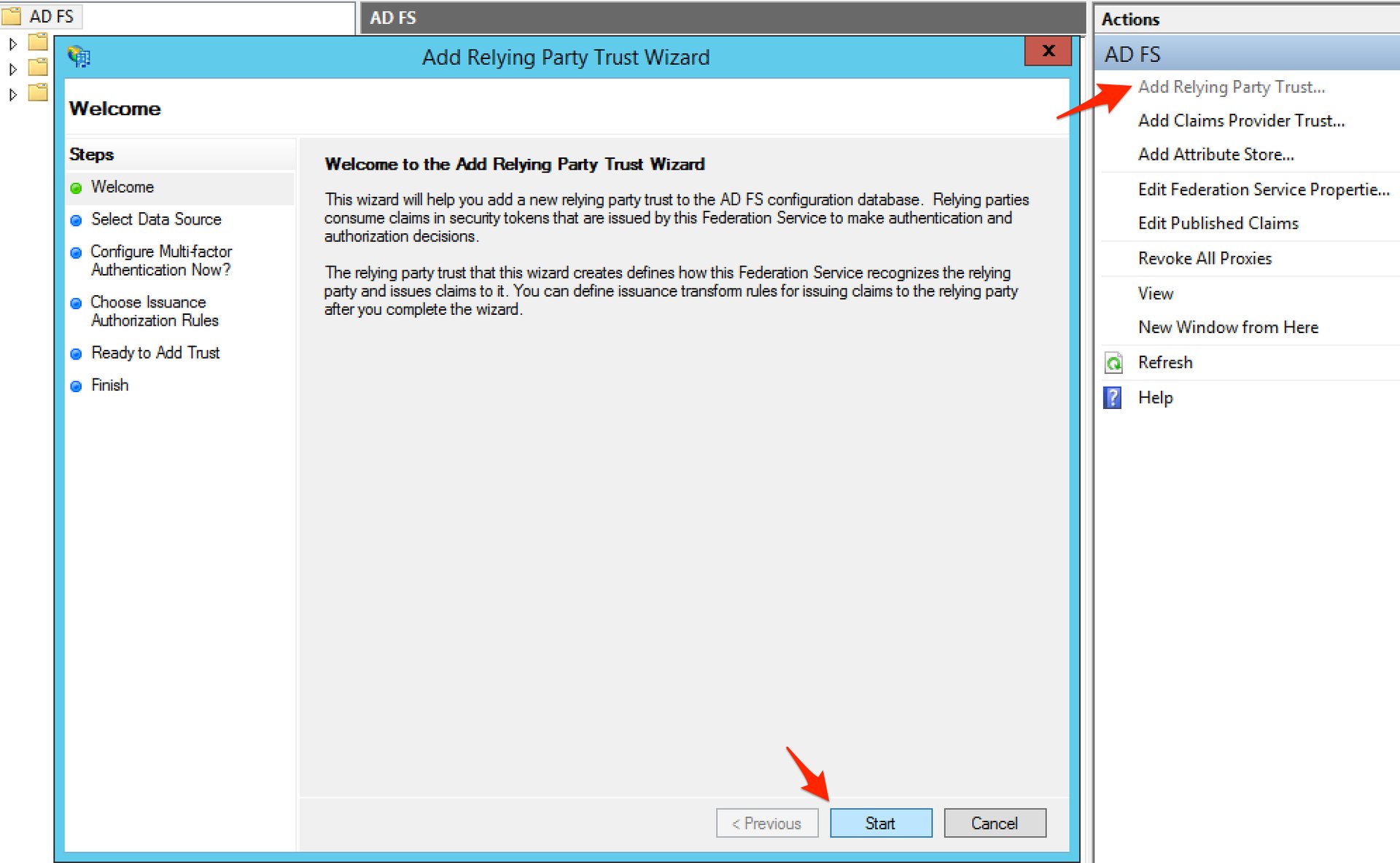
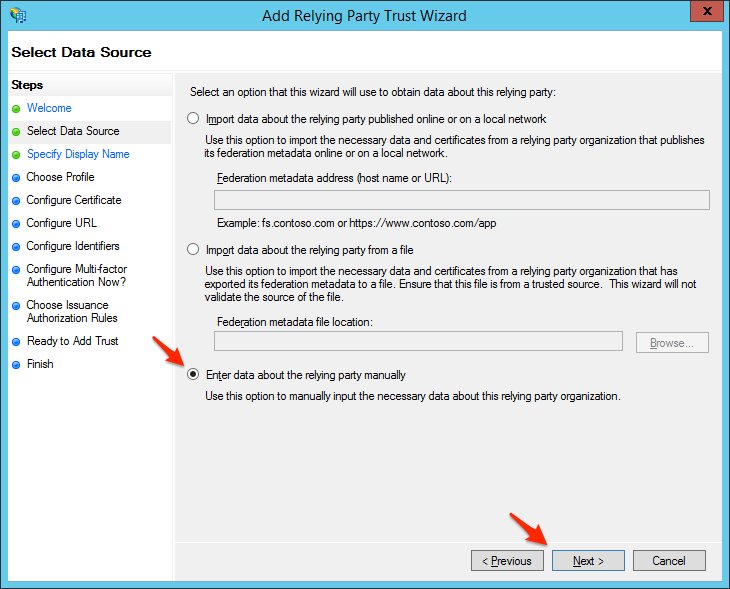
- Select Enter data about the relying party manually and click Next.
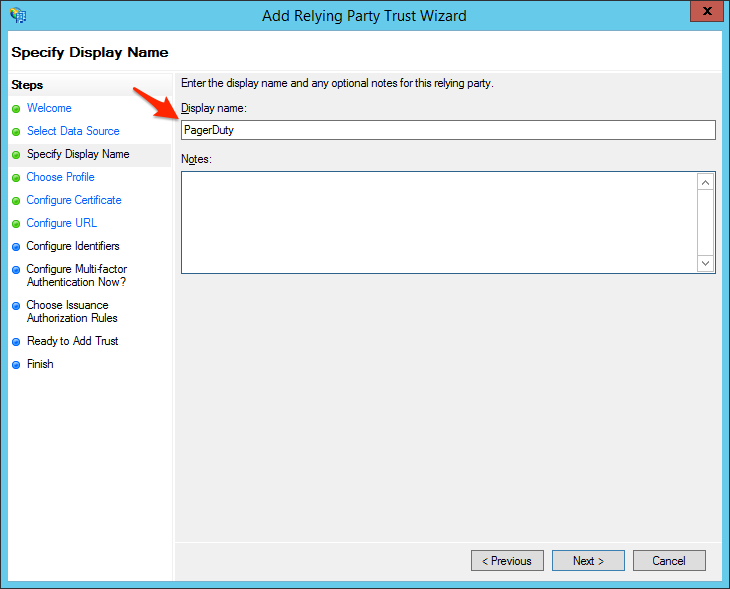
- Enter a Display name, such as PagerDuty, and click Next.
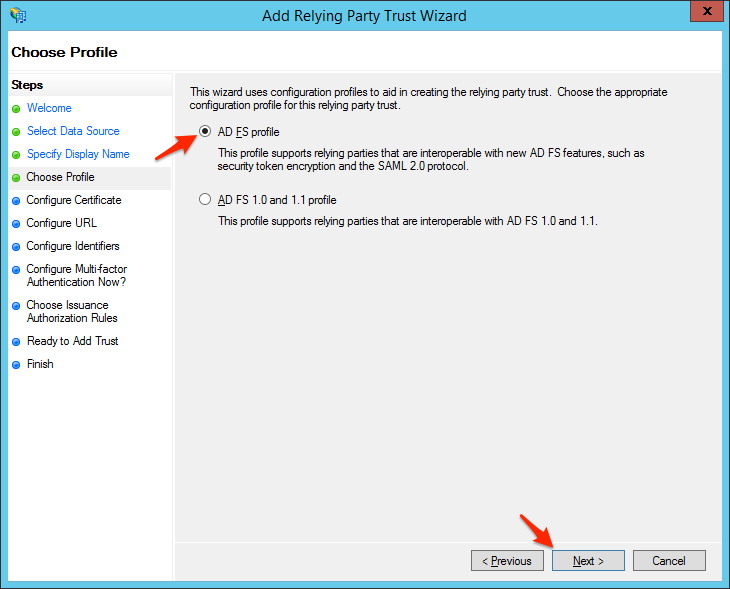
- Select AD FS profile and click Next.
- You will not need a token encryption certificate, so click Next to continue.
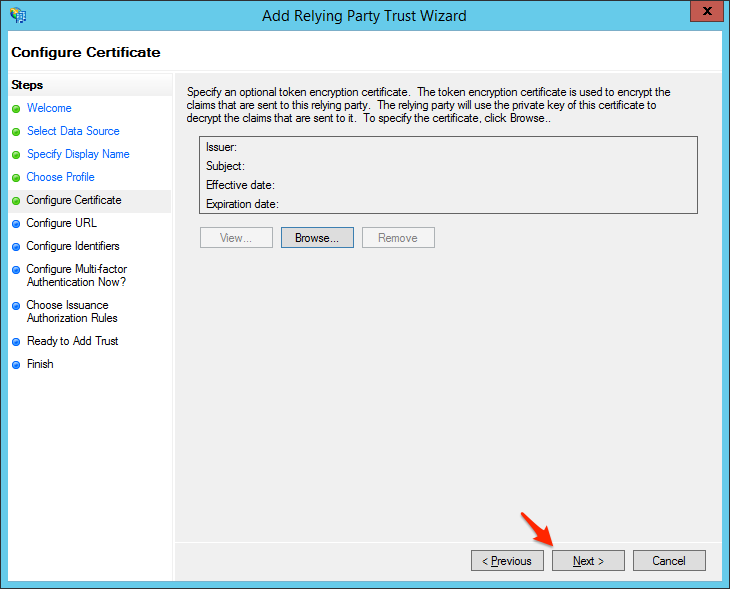
- Log in to your PagerDuty account, click the User Icon menu, select Account Settings and then select the Single Sign-on tab.
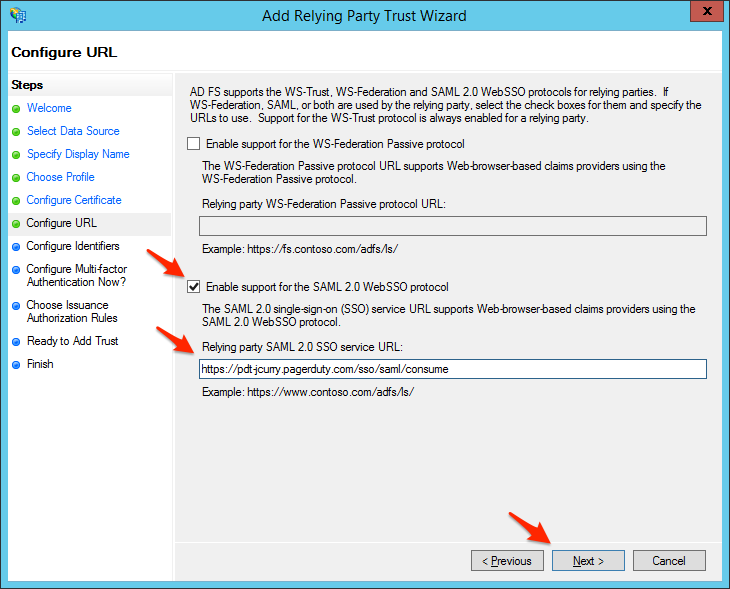
- Select the SAML radio button to configure Single Sign On in PagerDuty and then copy the SAML Endpoint URL to paste into the wizard.
- Back on your AD FS server, check the box to Enable support for the SAML 2.0 WebSSO protocol, then paste the URL you copied in the Relying party SAML 2.0 SSO service URL box and click Next. (Please Note, if your PagerDuty Subdomain contains EU, it is necessary to enter the full PagerDuty Subdomain including the eu, for example: https://(your_subdomain).eu.pagerduty.com)
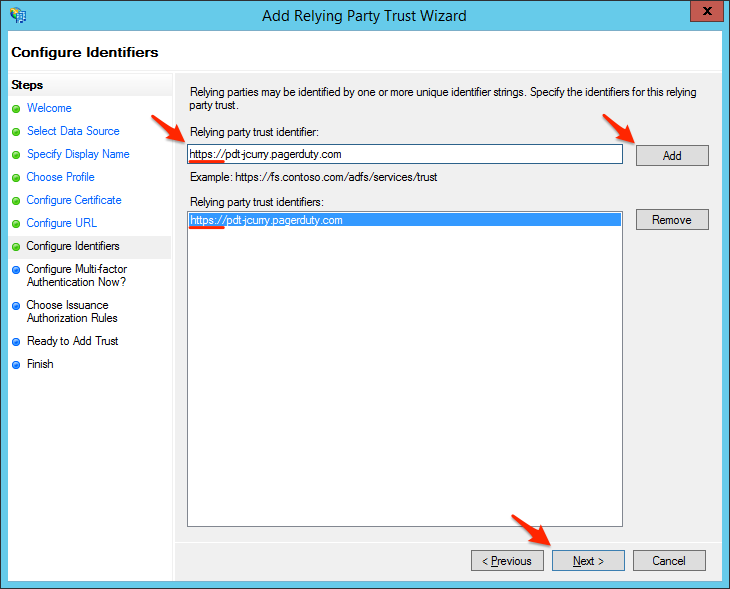
- Enter your PagerDuty subdomain in the Relying party trust identifier field - including https:// and with no trailing slash and click Next.Note: It is very important to enter your PagerDuty subdomain exactly as described. The integration will not work if you do not include https:// here, nor if you include a slash at the end of the URL. (Please Note, if your PagerDuty Subdomain contains EU, it is necessary to enter the full PagerDuty Subdomain including the eu, for example: https://(your_subdomain).eu.pagerduty.com)
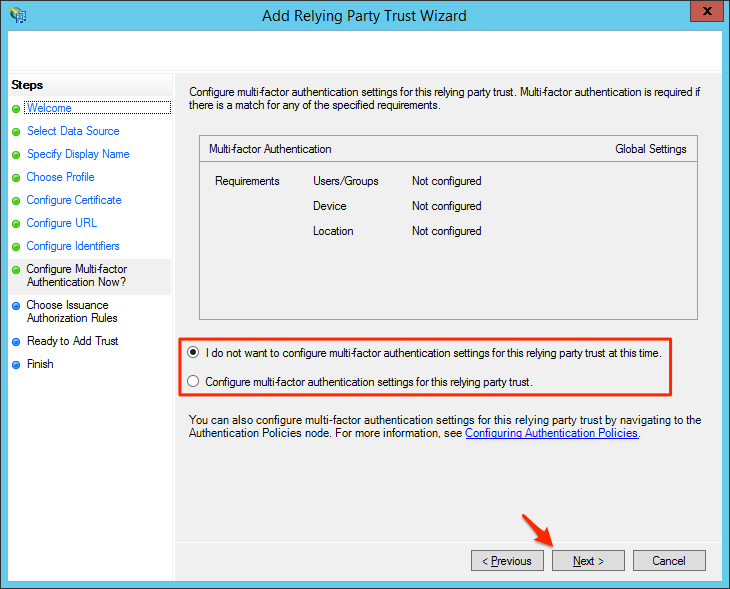
- Select your desired multi-factor authentication option for users and click Next.Note: Enabling multi-factor authentication will require additional steps that are outside the scope of this guide and will not be covered.
- Select Permit all users to access this relying party and click Next.Note: You may change this setting to deny by default and grant only specific users access to PagerDuty, however this process is outside the scope of this guide and will not be covered.
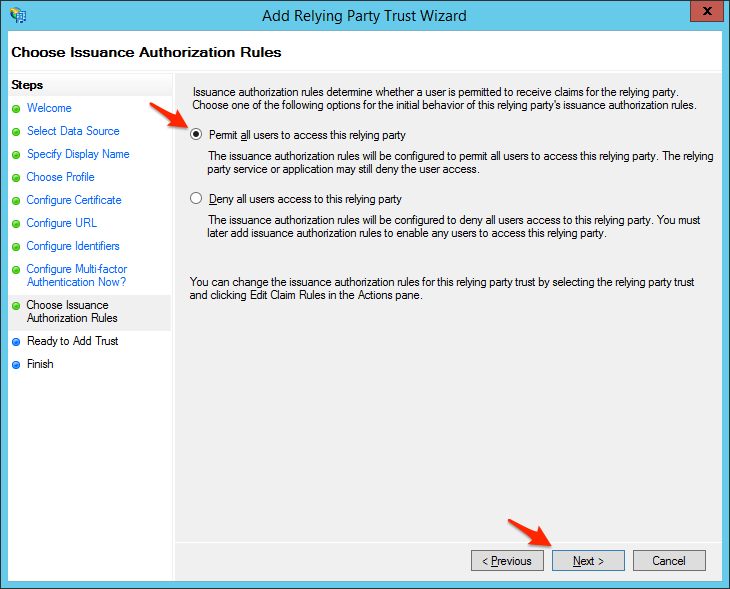
- Review your settings and click Next.
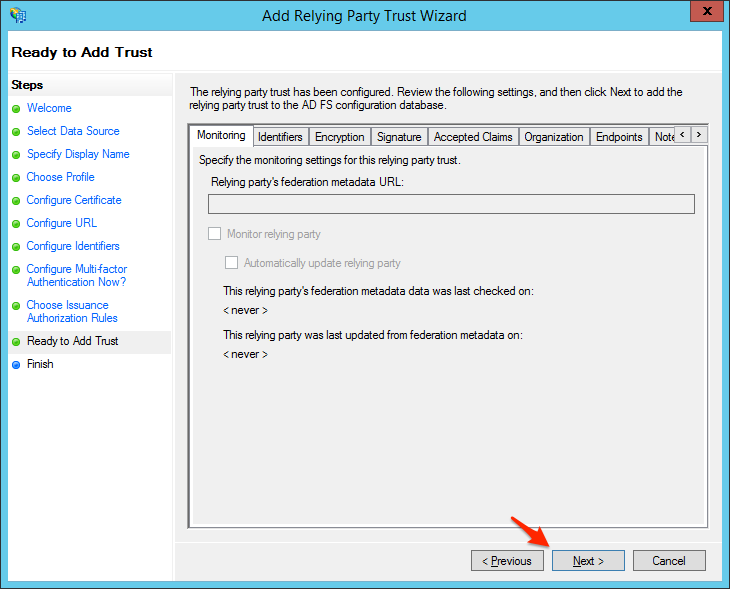
- Click Close to finish the wizard.
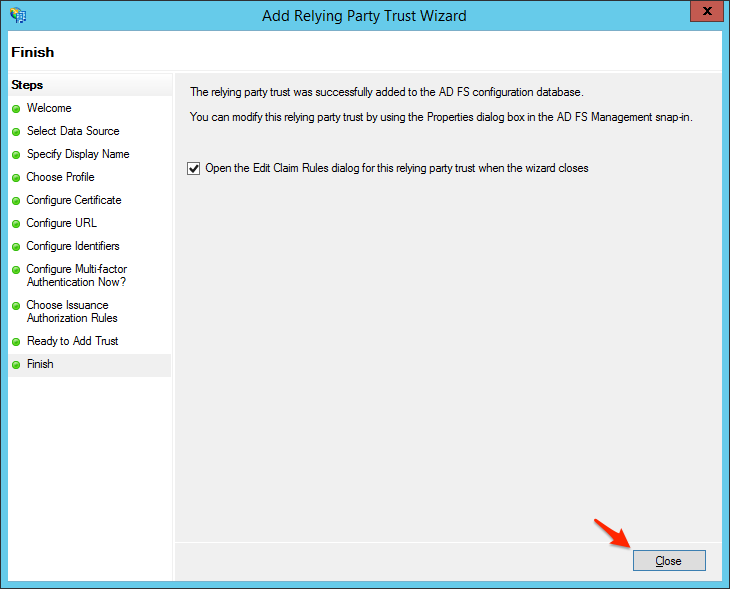
- Click Add Rule... on the Issuance Transform Rules tab.
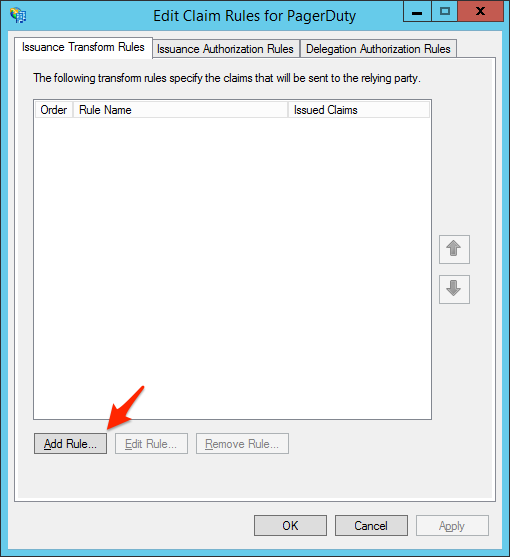
- Select Send LDAP Attributes as Claims and click Next.
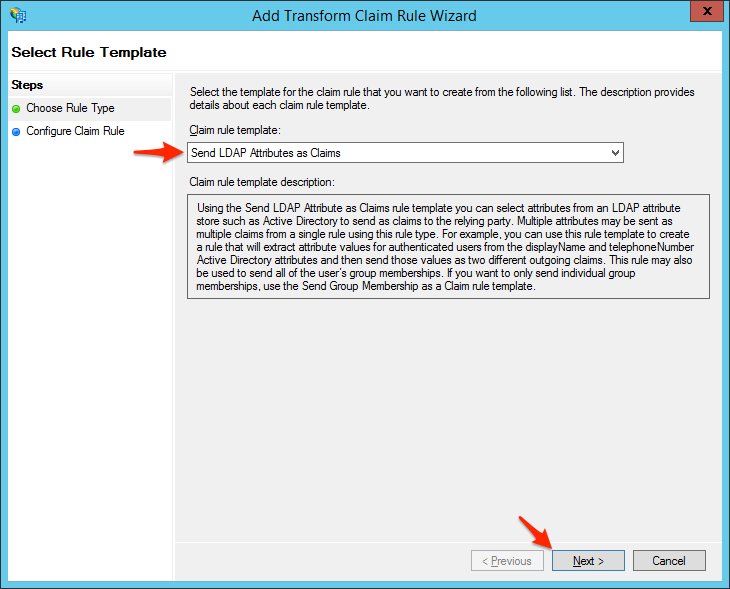
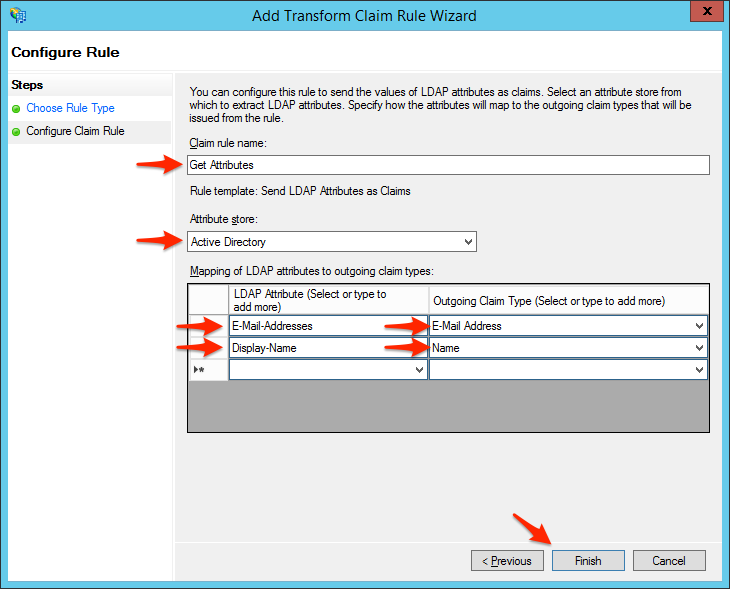
- Enter a Claim rule name, such as Get Attributes, then set the Attribute store to Active Directory, type in E-Mail-Addresses for the first LDAP attribute and set its outgoing type to E-Mail Address, and type in Display-Name for the second LDAP attribute and set its outgoing type to Name. Click Finish when you are done.Note: Is it very important to select the options with the exact same dashes and spaces documented after you begin typing in the specified value. The integration may not work if you select a variant which does not match exactly.
- Click Add Rule... on the Issuance Transform Rules tab again.
- Select Transform an Incoming Claim and click Next.
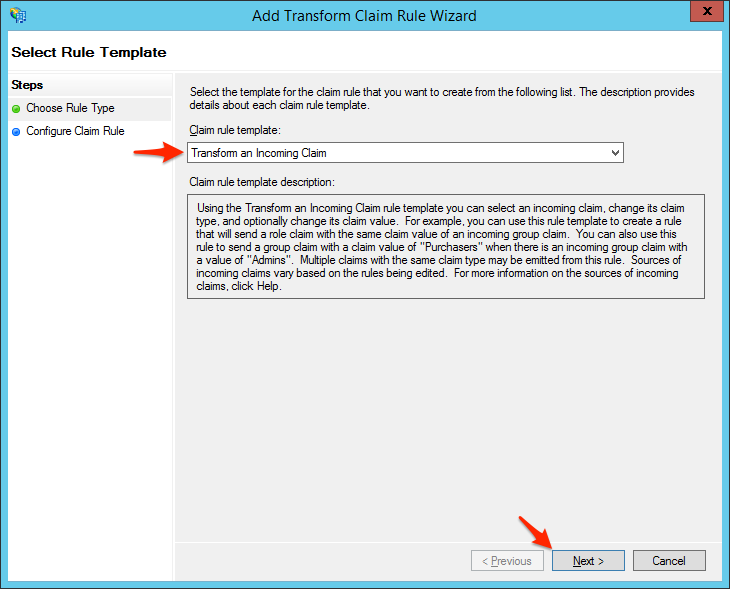
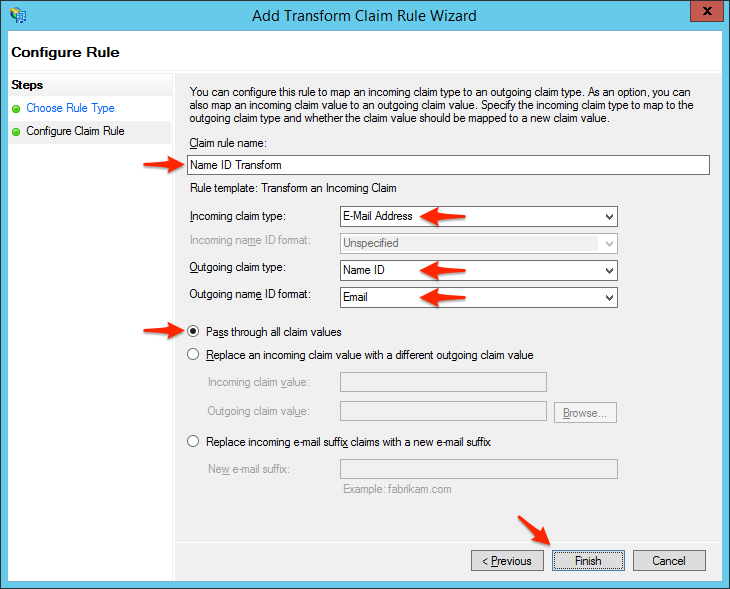
- Enter a Claim rule name, such as Name ID Transform, set Incoming claim type to E-Mail Address, set Outgoing claim type to Name ID, and set Outgoing name ID format to Email. Select Pass through all claim values and click Finish.Note: Is it very important to select the options with the exact same dashes and spaces documented after you begin typing in the specified value. The integration may not work if you select a variant which does not match exactly. For example, setting Outgoing claim type to NameID instead of Name ID will not allow you to set Outgoing name ID format to Email, and the integration will not work.
- Click Add Rule... on the Issuance Transform Rules tab again.
- Select Send Claims Using a Custom Rule and click Next.
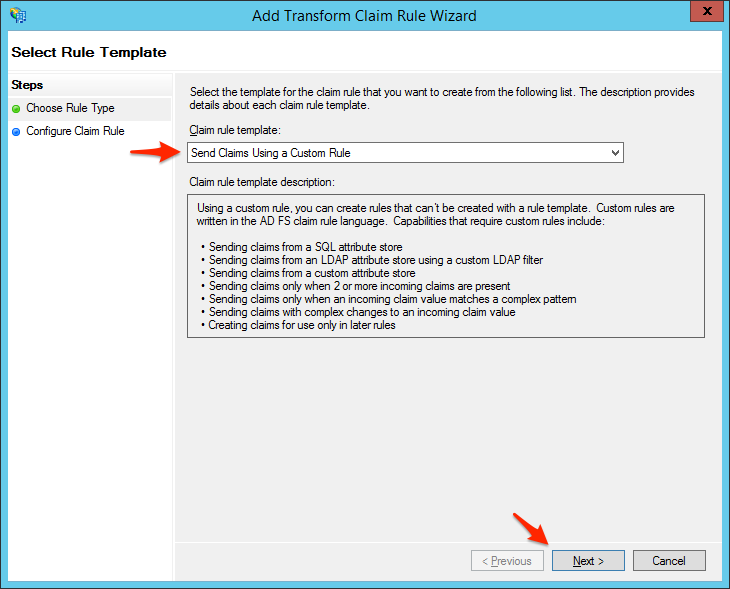
- Enter a Claim rule name, such as 'Name' Attribute Name Transform, then set Custom rule to the following: c:[Type == "https://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"] => issue(Type = "Name", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType);
Click Finish when you are done.
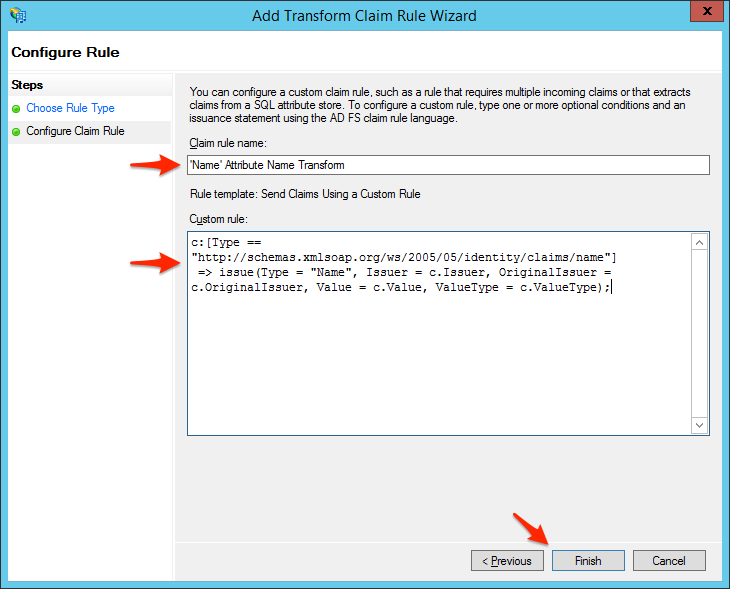
- Click OK on the Edit Claim Rules dialog.
- Go to Service > Certificates, select your Token-signing certificate and click View Certificate... in the Actions pane.
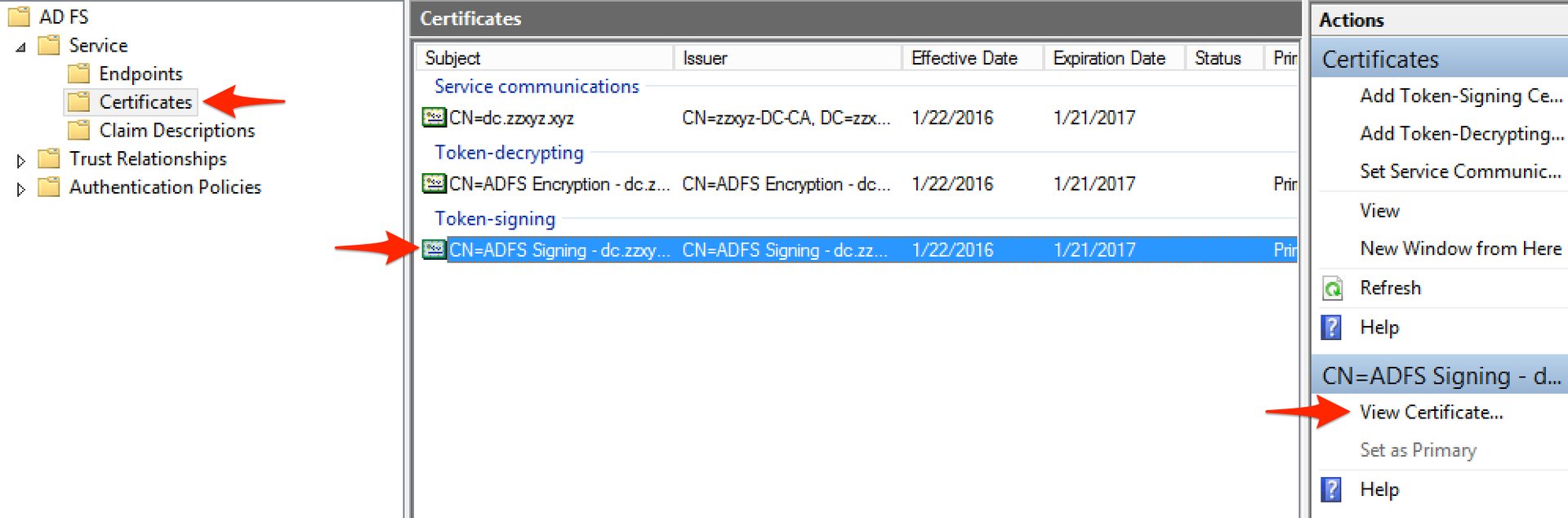
- Go to the Details tab and click Copy to File... and click Next on the Certificate Export Wizard introduction.
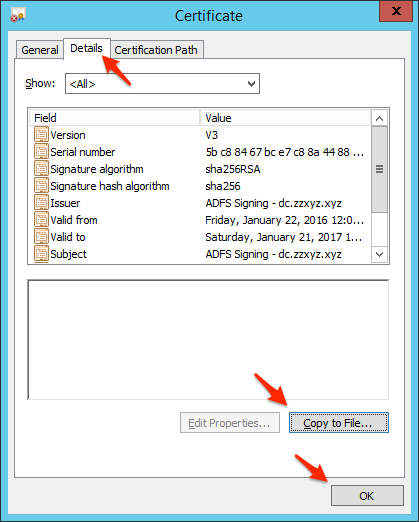
- Select Base-64 encoded X.509 (.CER) and click Next.
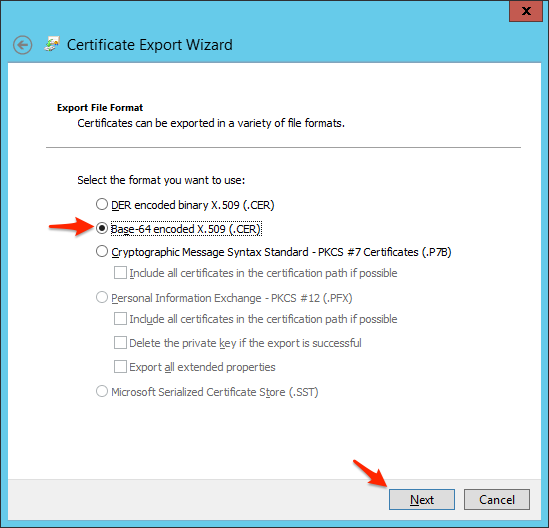
- Choose a location to save the certificate file, click Next and click Finish, OK, and OK again.
- Go to Authentication Policies and click Edit under Primary Authentication Global Settings.
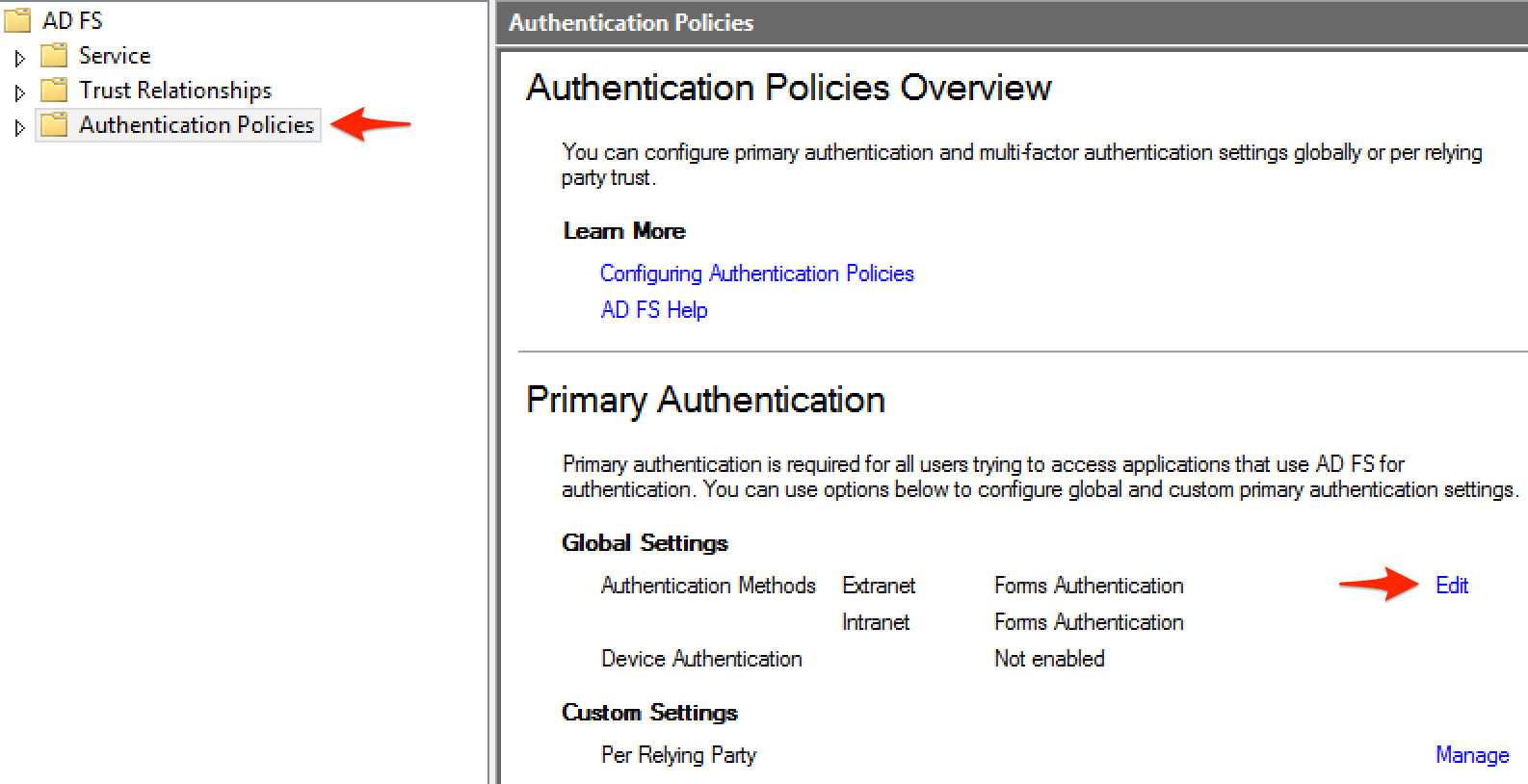
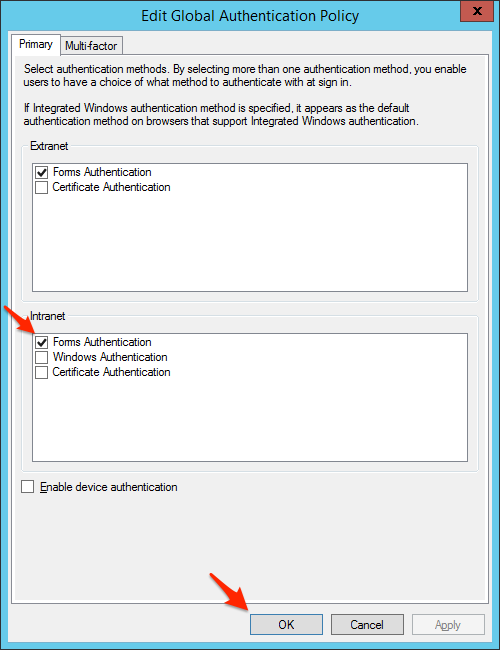
- Under Intranet, check Forms Authentication and click OK.Note: This is required for Windows Server 2012 R2. Previous versions of Windows already have Forms Authentication enabled by default. Also note that enabling Forms Authentication will apply to all sites configured, not just PagerDuty.An alternative option is to set forms as a fall back authentication method for intranet using the following PowerShell command: Set-AdfsGlobalAuthenticationPolicy –PrimaryIntranetAuthenticationProvider @('WindowsAuthentication','FormsAuthentication')
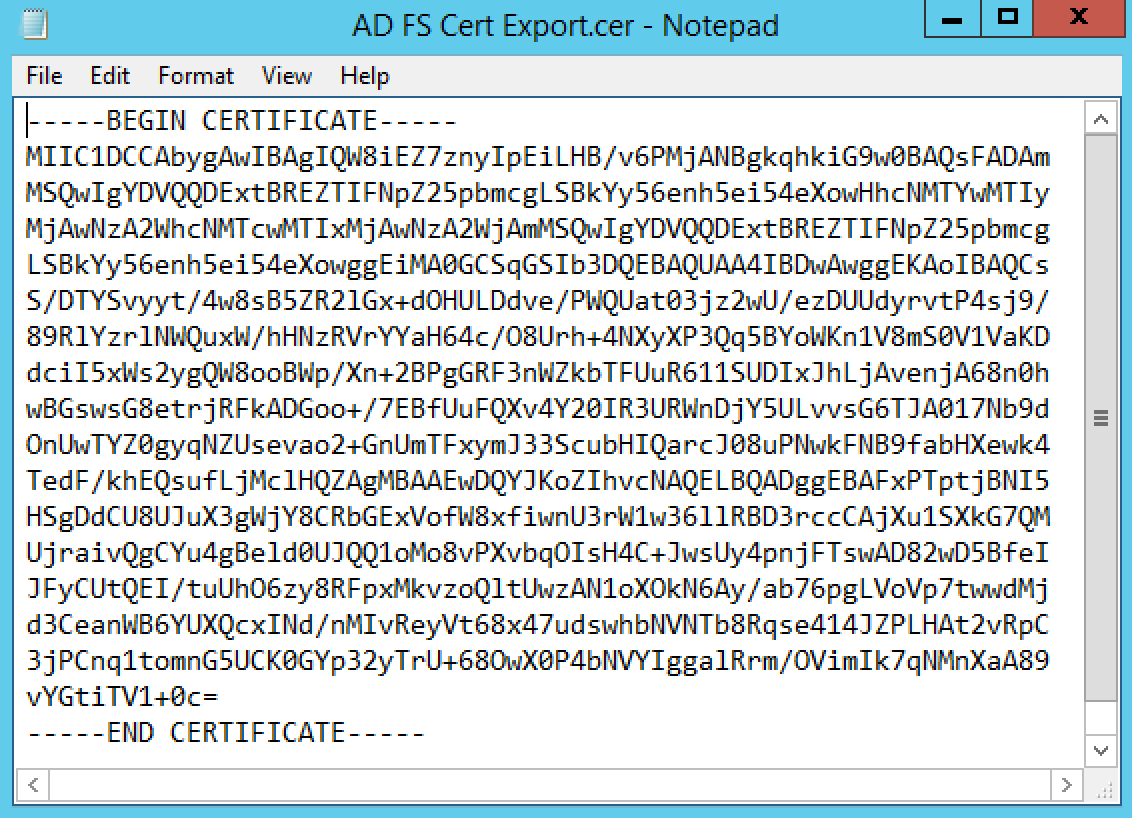
- Open the certificate file you exported in Notepad (or another plain text editor) and copy the contents.Note: You must include the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- headers when copying the certificate file contents. You should use Notepad or another plain text editor to open the certificate file; WordPad, Word, etc. are not plain text editors and may prevent you from copying the certificate correctly.
- In PagerDuty, paste the certificate in the X.509 Certificate field, then enter the Login URL for your AD FS service. The Login URL is usually the FQDN or IP or your server with /adfs/ls appended (i.e. https://login.company.com/adfs/ls).
- When you complete the steps in this guide and are done testing, you can return to this page to disable user logins via username and password. With auto provisioning enabled, you can allow SSO users to create a PagerDuty account without manual intervention, however please keep in mind that adding additional users will affect your billing if you go over the number of users included in your pricing plan. Click Save Changes when you are done on this page.
- Congratulations! You should now be able to login to PagerDuty using AD FS.
FAQ
Can the account owner log in without SSO if username and password authentication is disabled?
Even with this username and password authentication disabled for users, the Account Owner will always be able to login with their username and password as a backup option should you need to change the SSO configuration or disable it completely.
Why don't I see the Single Sign-on option when I go to Account Settings?
SSO is only available in accounts on our current Standard or Enterprise plans. Please contact our sales team if you are interested in upgrading your plan.
How do I create a Custom Claim Rule to include user roles/job titles in my configuration?
Follow the steps you used to create a Custom Claim Rule for 'Name' Attribute Name Transform, but set Claim Rule to the following:
c:[Type == "jobresponsibilities"] => issue(Type = "Role", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType);In this guide
Ready to get started?
Try any product on the Operations Cloud for free. No credit card required.
Try AIOps Try Automation Try Incident Management Try Customer Service OpsTag » Active Directory Federation Services Sso
-
How To Configure SSO With Microsoft Active Directory Federation ...
-
Configuring Single Sign-on (SSO) With ADFS - IT Glue
-
Configure Microsoft Active Directory Federation Services SSO
-
Set Up Single Sign-on (SSO) Using Active Directory Federation ...
-
AD FS 2016 Single Sign On Settings | Microsoft Docs
-
Set Up AD FS For Microsoft 365 For Single Sign-On
-
Set Up SSO With Active Directory Federation Services (AD FS)
-
Single Sign-On: The Difference Between ADFS Vs. LDAP | Okta
-
Configuring Active Directory Federation Services - IBM
-
Active Directory Federation Services Integration Guide Overview
-
Enabling Single Sign-On (SSO) Using Active Directory Federation ...
-
Active Directory Federation Services (ADFS) Setup Guide
-
Configuring Active Directory Federation Services (ADFS) With Flex
-
Steps To Configure SAML 2.0 SSO With Microsoft Active Directory ...