CHAP (Challenge-Handshake Authentication Protocol) By
Maybe your like
- Home
- Identity and access management
 By
By - Peter Loshin, Former Senior Technology Editor
What is CHAP (Challenge-Handshake Authentication Protocol)?
CHAP (Challenge-Handshake Authentication Protocol) is a challenge and response authentication method that Point-to-Point Protocol (PPP) servers use to verify the identity of a remote user. CHAP authentication begins after the remote user initiates a PPP link.
CHAP enables remote users to identify themselves to an authenticating system, without exposing their password. With CHAP, authenticating systems use a shared secret -- the password -- to create a cryptographic hash using the MD5 message digest algorithm.
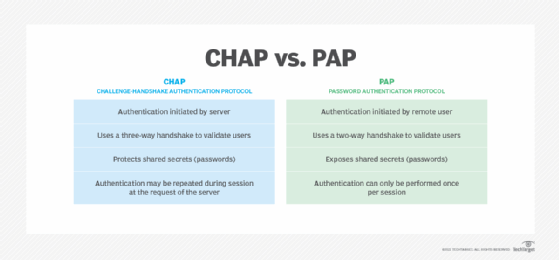
CHAP uses a three-way handshake to verify and authenticate the identity of the user, whereas the Password Authentication Protocol (PAP) uses a two-way handshake for authentication between the remote user and PPP server.
Designed to be used with PPP for authenticating remote users, CHAP is applied periodically during a remote session to reauthenticate the user. PAP and CHAP are primarily intended for remote connections over dial-up lines or switched circuits, as well as for dedicated links.
PAP and CHAP are commonly used for negotiating a network connection to an internet service provider. CHAP is specified in Request for Comments 1994.
How does CHAP work?
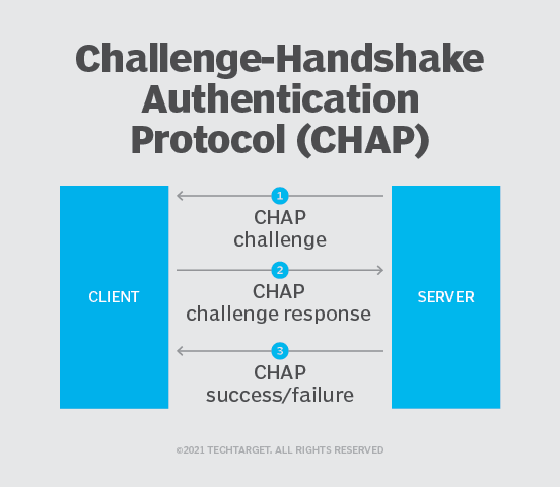
Here's how CHAP works:
- After the link is made, the server sends a challenge message to the connection requestor.
- The requestor responds with a value obtained by using a one-way hash function known as MD5.
- The server checks the response by comparing it with its own calculation of the expected hash value. If the values match, the authentication is acknowledged; otherwise, the connection is usually terminated.
The server can send a new challenge to the requestor randomly during the session to reauthenticate the requestor. Steps 1 through 3 are then repeated.
At any time, the server can request the connected party to send a new challenge message. Because CHAP identifiers are changed frequently and authentication can be requested by the server at any time, CHAP provides more security than PAP.
Types of CHAP packets
PPP carries CHAP packets between the authenticator and the requestor. CHAP packets consist of a header, which includes the following:
- Code field, which contains an eight-bit code identifying the type of CHAP packet being sent -- valid values are 1 to 4;
- Identifier field, which is an arbitrary eight-bit ID identifying the packet as belonging to an authentication sequence;
- Length field, which contains the number of bytes in the CHAP packet; and
- Data field, which includes any data being requested or submitted and values depending on the type of CHAP packet it is being carried in.
Further reading
CHAP and PAP were among the first attempts to implement secure remote access, and understanding the differences between CHAP and PAP is just the first step.
CHAP integrates with the Remote Authentication Dial-In User Service, or RADIUS, protocol. Kerberos offers a more sophisticated and secure tool for remote user authentication.
Learning the differences between CHAP and Extensible Authentication Protocol, Lightweight Extensible Authentication Protocol and Wi-Fi Protected Access version 2 protocol will help IT pros make the best decision.
CHAP works with four different types of packet. Each packet is identified by the value of its Code field, as follows:
- The authenticating system -- usually a network access server or switch -- sends a CHAP Challenge packet to start the authentication process. After a PPP session is initiated, the system or network being accessed can demand that the remote user authenticate. The Challenge includes the authenticator's host name.
- The remote user's system must send a CHAP Response packet in response to a Challenge. The remote system sends a secure hash based on the remote user's password in the Response packet. The authenticator compares the hash of the user's password with the expected value. The remote user is authenticated if they match; otherwise, the authentication fails.
- The authenticating system -- the network access server-- sends a CHAP Success packet if the remote user's hash matches the hash expected by the server.
- The authenticating system sends a CHAP Failure packet if the remote user's password hash does not match the value sent by the user.
If the remote system fails to respond to a Challenge packet, the authenticator can repeat the process. The authenticator terminates the remote user's access if they can't authenticate.
CHAP vs. PAP
CHAP is a more secure procedure for connecting to a system than PAP.
The PAP and CHAP authentication schemes were both originally specified for authenticating remote users connecting to networks or systems using PPP. CHAP's three-way handshake protocol provides stronger protection against password guessing and eavesdropping attacks than PAP's two-way handshake.
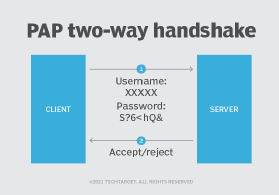
Authenticating with PAP requires the remote user to submit their username and password, and the authenticating system then either permits or denies the user access based on those credentials.
CHAP secures the authentication process by using a more sophisticated protocol. CHAP implements a three-way handshake protocol to be used after the host establishes a PPP connection with the remote resource.
PAP defines a two-way handshake for a remote user to initiate remote access:
- The remote system sends a username and password, repeating the transmission until the network access server responds.
- The network access server transmits an authentication acknowledgement if the credentials are authenticated. If the credentials are not authenticated, the network access server sends a negative acknowledgment.
While PAP may be used as a bare minimum protocol to enable a remote user to initiate a network connection, CHAP provides a more secure authentication protocol.
Continue Reading About CHAP (Challenge-Handshake Authentication Protocol)
- The top 7 identity and access management risks
- What is secure remote access in today's enterprise?
- IPsec vs. SSL VPN: Comparing speed, security risks and technology
- Wireless network configuration basics: 5 steps to follow
- What are the most common digital authentication methods?
Related Terms
What is a message authentication code (MAC)? How it works and best practices A message authentication code (MAC) is a cryptographic checksum applied to a message to guarantee its integrity and authenticity. See complete definition What is biometric authentication? Biometric authentication is a security process that relies on the unique biological characteristics of individuals to verify ... See complete definition What is identity and access management? Guide to IAM No longer just a good idea, IAM is a crucial piece of the cybersecurity puzzle. It's how an organization regulates access to ... See complete definitionDig Deeper on Identity and access management
-
![]()
What is Point-to-Point Protocol over Ethernet (PPPoE)?
 By: Scott Robinson
By: Scott Robinson -
![]()
Use these 6 user authentication types to secure networks
 By: Kyle Johnson
By: Kyle Johnson -
![]()
Health Literacy, Care Access Barriers to Cervical Cancer Screening
 By: Sara Heath
By: Sara Heath -
![]()
NVMe-oF over IP: A complete SAN platform
- 3 Transformative VDI Use Cases for Hybrid Work –Dell Technologies
- Hybrid Work Drives New Criteria for VDI and DaaS –Dell Technologies
- See More
- The 5 Different Types of Firewalls Explained –TechTarget
- 8 Reasons Why Your IT Organization Needs SASE –Cato Networks
- Networking
- CIO
- Enterprise Desktop
- Cloud Computing
- Computer Weekly
- 5 principles of change management in networking
Network change management includes five principles, including risk analysis and peer review. These best practices can help ...
- How network efficiency advances ESG goals
From SDN to green electricity, network optimization plays a critical role in helping enterprises reduce emissions, cut costs and ...
- How to build a private 5G network architecture
A private 5G network can provide organizations with a powerful new option for their wireless environments. Here are the major ...
- 12 top business process management tools for 2026
BPM platforms are becoming a business transformation engine as vendors infuse their tools with powerful AI and automation ...
- What Big Tech's AI spending means for your IT budget
Hyperscalers are spending billions on AI. CIOs can't match that scale -- but they can adopt smarter budgeting strategies to ...
- Top CIO conferences, according to the CIOs who attend them
CIOs highlight the conferences they prioritize, including Gartner forums, Dreamforce, AI Summit and SC. These events help them ...
- How Windows 11 Safe Mode works and when to use it
Windows 11 Safe Mode gives IT leaders a reliable way to diagnose failures, restore access to broken systems and strengthen ...
- How Windows 11 Print Management can fix printer issues
IT admins can use Print Management in Windows 11 to manage all printers connected to a device, troubleshoot problems and restart ...
- How to migrate applications to Windows 11
As Windows 10 support ends, organizations must plan Windows 11 migrations carefully. Assess apps, data and device configurations ...
- GenAI drives $119B cloud revenue in Q4
Q4 cloud infrastructure service revenues reach $119.1 billion, bringing the 2025 total to $419 billion. See how much market share...
- Cloud infrastructure suffers AI growing pains
Will $5 trillion in AI infrastructure investment be enough? Cloud providers facing that question must also yield a return, ...
- 8 reasons why IT leaders are embracing cloud repatriation
As IT leaders aggressively re-allocate capital to fund new AI initiatives, repatriation offers both savings and greater control, ...
- UK direct-to-device satellite connectivity takes off with Virgin Media O2
Leading UK mobile operator switches on pace comms service in a move to make UK the first country in Europe to go live with ...
- NTT Data, Ericsson team to scale private 5G, physical AI for enterprises
Global comms tech provider forges global partnership with business and technology services firm to establish 5G as the ...
- Connectivity, AI drive fleet safety, productivity and decision-making
Report into state of fleet technology across US reveals three key priorities for the year: increasing productivity, reducing ...
Tag » What Does Chap Stand For Networking
-
What Is CHAP? - Security Wiki - Double Octopus
-
Challenge-Handshake Authentication Protocol - Wikipedia
-
Challenge Handshake Authentication Protocol (CHAP)
-
What Is The Challenge Handshake Authentication Protocol (CHAP)?
-
Peer Authentication Using PAP And CHAP
-
Challenge Handshake Authentication Protocol (CHAP)
-
What Is The Difference Between PAP And CHAP - Pediaa.Com
-
Understanding And Configuring PPP CHAP Authentication - Cisco
-
What Is A Challenge-Handshake Authentication Protocol (CHAP)?
-
CHAP And PAP - CompTIA Security+ SY0-401: 5.2 - Professor Messer
-
CHAP Stands For? - Quiz
-
What Is The Chap System Network Security?
-
What Is PAP? What Is CHAP? What Is Realm Authentication?
-
Network Authentication - An Overview | ScienceDirect Topics



