Firewall Ports For AD Domain Join - Devopstales
Maybe your like
-
- Firewall Ports required to join AD Domain (Minimum)
- Optional Ports
- Firewall Rules in pfesense Firewall
In this post I will show you what port you need to enable for AD Domain Join.
Firewall Ports required to join AD Domain (Minimum)
Windows 10 Client can join to Windows 2019 AD Domain with the following Ports allow in Firewall
- TCP 88 (Kerberos Key Distribution Center)
- TCP 135 (Remote Procedure Call)
- TCP 139 (NetBIOS Session Service)
- TCP 389 (LDAP)
- TCP 445 (SMB,Net Logon)
- UDP 53 (DNS)
- UDP 389 (LDAP, DC Locator, Net Logon)
- TCP 49152-65535 (Randomly allocated high TCP ports)
Without TCP High Ports open the following Message appear even join to domain successfully:
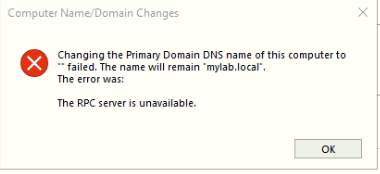
there is a lot of TCP high ports are blocked in Firewall:
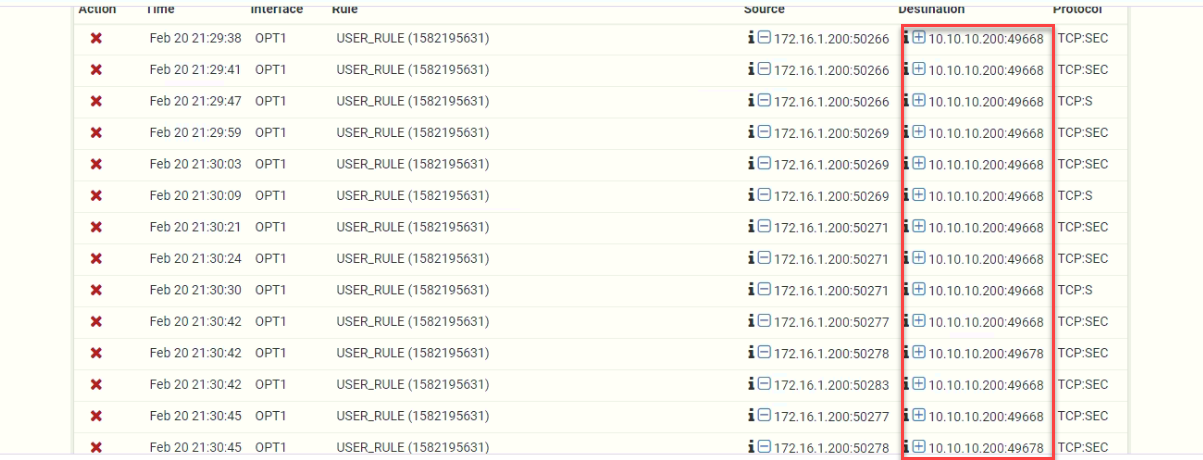
Optional Ports
- UDP 123 (NTP)
- TCP 53 (DNS)
- TCP 464 ( Kerberos Password V5 – Used when user change their password from desktop)
- UDP 137 (NetBIOS Name Resolution)
- UDP 138 (NetBIOS Datagram Service)
- TCP 636 (LDAP SSL)
- UDP 636 (LDAP SSL)
- TCP 3268 (Global Catalog)
User can still change their password successfully even thought TCP 464 is blocked in Firewall
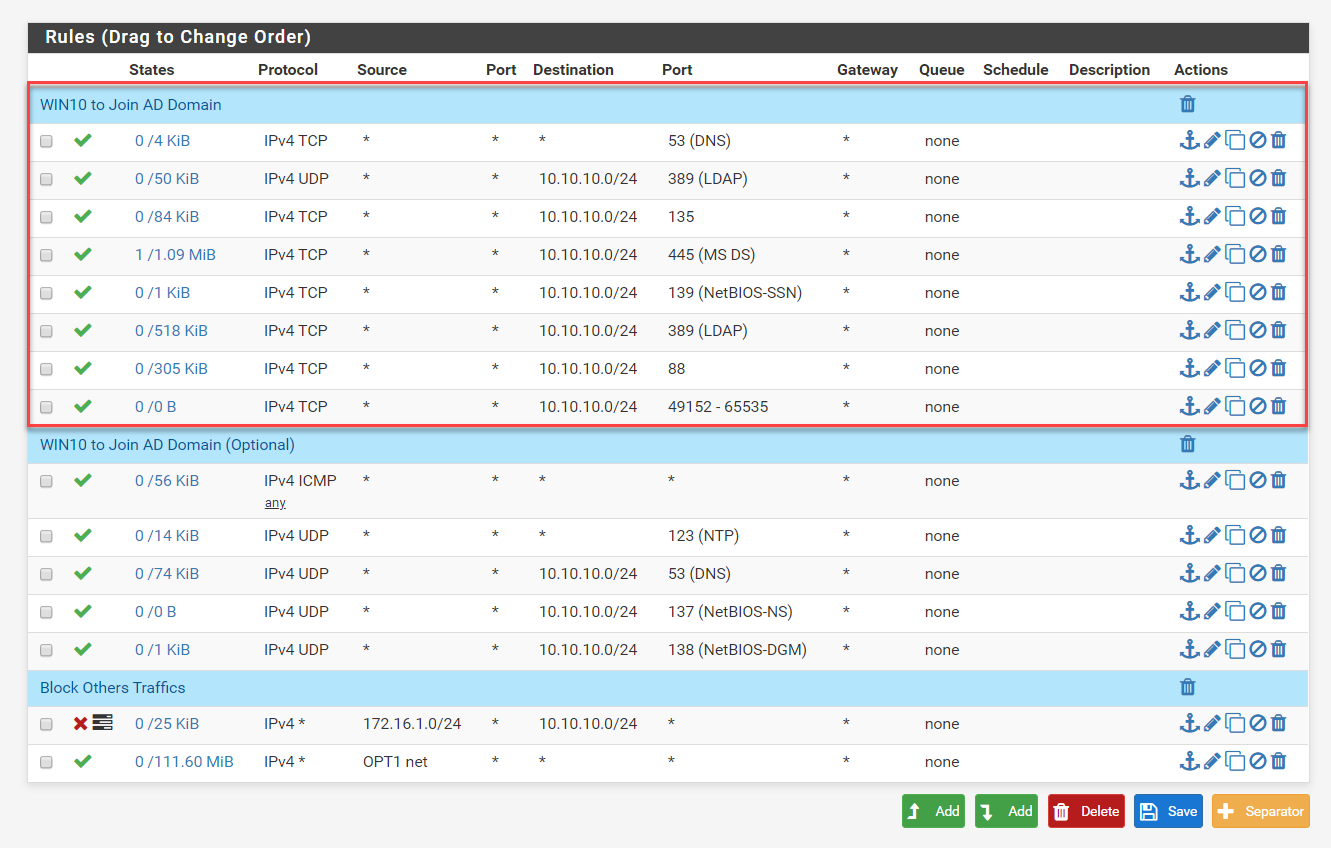
Firewall Rules in pfesense Firewall
Your support is our everlasting motivation, that cup of coffee is what keeps us going!
As we continue to grow, we would wish to reach and impact more people who visit and take advantage of the guides we have on our blog. This is a big task for us and we are so far extremely grateful for the kind people who have shown amazing support for our work over the time we have been online.
Thank You for your support as we work to give you the best of guides and articles. Click below to buy us a coffee. 
Blog Series
- cluster-mesh (5)
- container runtimes (20)
- k3s (7)
- k8s-authentication (9)
- k8s-gitops (7)
- k8s-lessons (14)
- k8s-network (31)
- k8s-operators (10)
- k8s-security (65)
- kubernetes (31)
- mikrotik (5)
- virtualization (3)
Social
GitHub DockerHub ArtifactHub OperatorHub.io helm-chartsRecent Posts
- Implementing Mutual TLS (mTLS) with Traefik Ingress Controller: Per-Ingress Configuration
- Implementing Mutual TLS (mTLS) with NGINX Ingress Controller: Per-Ingress Configuration
- Migrating from NGINX Ingress Controller to Traefik: A Step-by-Step Guide
- Migrating from NGINX Ingress Controller to HAProxy: A Step-by-Step Guide
- Why Kubernetes Pods See Host Resources (And How to Fix It)
- Kubernetes Cluster API: a step by stap guide
- Automatic Kubernetes Certificate Renewal
- Known Issues of Azure Key Vault AKS integration and resolutions
- What is RBAC in Kubernetes?
- Tekton Basics
Tags
2FA Active Directory Admission Controller AKS Alerta AlmaLinux Ansible Ansible Tower AWS AWX Azure Backup BGP Calico CentOS Centreon Ceph Certificate Authority Chef Cilium Cloud Sql Cluster Cluster-Mesh CNI-Genie Container Runtimes Containerd CoreDNS Cosign CRI-O Debian Devops DNS Docker Docker Compose Ebpf ECR EKS Elasticsearch Falco Fedora Fedora CoreOS Firecracker Flannel Foreman GCP GitHub Gitlab Gitlab-Runner Gitops GKE GNS3 Google Cloud Platform Grafana Graylog Group Policy Gvisor HA HAproxy Harbor HashiCorp Vault Helm Helm-Controller Helm2 Helm3 HP Httpd Icinga ILO Influxdb Ingress Ipmitool Ipsec Jitsi K0S K3S K8s Kafka Kata-Container Katello Keepassxc Keycloak Kube-Apiserver Kube-Openid-Connect Kube-Proxy Kube-Vip Kubedash Kubernetes Kyverno Linkerd Logging Loki Mattermost MetalLB Microk8s Mikrotik Mtls Multus Mutating Webhook Mysql Naemon Nagios Nerdctl Nextcloud Nexus OSS Nginx Nmstate NoSQL Notary Oauth2 Oidc OpenID Openproject Openshift Openshift 3.11 Openshift 4 OpenVPN Operator Opnsense Pfsense Postgresql PowerShell Privacyidea Prometheus Proxmox Proxy PXE RADIUS Rancher RBAC Redmine Registry Rke2 Routeros Rsyslog Rundeck S3 Seccomp Secuity Security SIEM Skupper Sonarqube Spacewalk Squid Sso Submariner Supermicro Tekton Telegraf Terraform Traefik Trivy-Operator Ubuntu Unifi Unifi Controller Vagrant Veeam Backup Vmware Volume Expansion VSphere Vxlan Wazuh Wildfly Windows ZFS This website makes use of third-party cookies. Learn More OkayTag » Ad Dc Ports
-
More Information
-
Ports To Be Opened For AD / DC - TechNet - Microsoft
-
Complete List Of Active Directory Ports And What They Do Explained
-
Cyber Security Awareness Month - Day 27 - Active Directory Ports
-
Firewall Ports Required To Join AD Domain - AventisTech
-
Active Directory Firewall Ports – Let's Try To Make This Simple
-
A Guide To Active Directory Ports And Authentication Protocols
-
Ports Required To Talk To Windows DC For AD Authentication
-
Domain Controllers Required Ports: Use PowerShell To Check If They ...
-
Active Directory Ports: Service And Network Port Requirements For ...
-
What Firewall Ports For Active Directory?
-
Firewall Ports To Open For Active Directory Communication
-
Change The Default Port For The Active Directory Server
-
Samba AD DC Port Usage - SambaWiki