Refresh Membership In AD Security Groups Without Reboot Or Logoff
Maybe your like
 Refresh membership in AD security groups without reboot or logoff Home Blog Refresh membership in AD security groups without reboot or logoff
Refresh membership in AD security groups without reboot or logoff Home Blog Refresh membership in AD security groups without reboot or logoff 4sysops - The online community for sys and AI ops
- Purging Kerberos tickets
- Updating memberships for users
- Author
- Recent Posts
- Assign recommended Windows security settings with the free Harden Windows Security app - Wed, Jun 11 2025
- Activate Windows authentication with a PIN - Mon, Jun 2 2025
- Hyper-V Quick Create: Deploy custom VM images - Mon, May 19 2025
If you make a server a member of an AD group, for example, to include it in the security filtering of a GPO or to grant it permissions to request a certificate, it simply may not be possible to restart it immediately afterwards. However, a reboot is usually necessary to update computer membership in AD groups.
Read 4sysops without ads for freePurging Kerberos tickets
You can bypass the reboot by renewing the Kerberos ticket for the computer with klist.exe. If you run
klist.exe sessions | findstr /i %COMPUTERNAME%on a command prompt, you will see that the so-called low part of the local computer's LogonID always has the value 0x3e7, while 0x3e4 belongs to the network service. The corresponding cached Kerberos tickets can be displayed with
klist.exe -li 0x3e7
The low part of the local computers LogonID always has the value 0x3e7
After adding the computer account to a new security group in AD, you can remove them using the purge parameter:
klist.exe -li 0x3e7 purge
Invoking klist.exe li 0x3e7 purge deletes the tickets for the computer account
Subsequently, by executing
gpupdate /forceyou will get new tickets. If you run
klist.exe -li 0x3e7again and compare the output with the earlier use of this command, you will see that the timestamps of the Kerberos tickets have changed.
Using Read 4sysops without ads for free
gpresult /r /scope computeryou can display the groups in which the local computer is a member. However, this command usually does not reflect changes after the ticket was renewed, regardless of whether the account was added to or removed from a group.
However, if you use an AD group for GPO security filtering, then the change has an immediate effect here and is also visible in the output of gpresult. The same applies to the permissions on other resources.
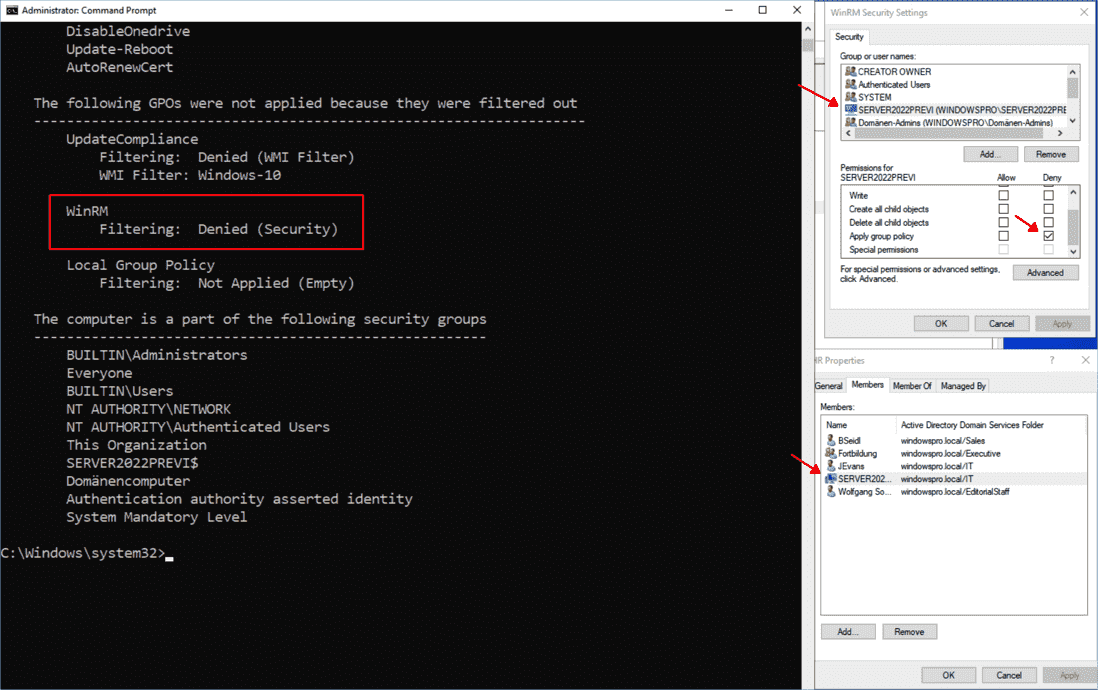
Server2022Preview has been added to the HR group which is not eligible for the WinRM GPO. gpresult does not show the HR group but the effect on filtering.
Updating memberships for users
While servers often cannot be restarted just to update membership in AD groups, it is usually not a major problem for users to log off and on again to gain access to certain resources by changing group memberships.
However, if you want to avoid a logoff, klist.exe can help here as well. In this case, after the user account has been added to a new group, execute Read 4sysops without ads for free
klist purgeon a command line without elevated privileges. The program prints the LogonID of the current user and confirms that the Kerberos tickets for this user have been deleted. To get new ones, you can start another instance of cmd.exe using runas.

After the klist purge a new instance of cmd.exe shows the membership of the user in the group HR
If you run
whoami /groupsthere, then the change in the group memberships should already be noticeable. Accordingly, the user should also be able to access a network share, for example via the FQDN of the server, which he was denied before he was added to the new AD group.
It is obvious that the described solution works only for services that support Kerberos. With NTLM authentication, there is no way around rebooting or logging out.
6 CommentsJoin our IT community and read articles without ads!
Related Articles-
 +
+ Blocking user SyncJacking (account hijacking) in Microsoft Entra Connect
 IT Experts Tue, Jan 27 2026Tue, Jan 27 2026 active directory, security, entra 0
IT Experts Tue, Jan 27 2026Tue, Jan 27 2026 active directory, security, entra 0 -
 +
+ Microsoft Entra PowerShell v1.2.0 brings Agent Identity Blueprint management and new automation features
 IT Experts Wed, Jan 21 2026Wed, Jan 21 2026 powershell, active directory, AI, AI agents, entra 0
IT Experts Wed, Jan 21 2026Wed, Jan 21 2026 powershell, active directory, AI, AI agents, entra 0 -
 +
+ Disable weak RC4 encryption on Active Directory domain controllers to prevent Kerberoasting attacks exploiting Kerberos vulnerability CVE-2026-20833
 IT Experts Tue, Jan 20 2026Tue, Jan 20 2026 encryption, active directory, security 0
IT Experts Tue, Jan 20 2026Tue, Jan 20 2026 encryption, active directory, security 0 -
-with-Microsoft-Entra-Verified-ID-on-iPhone-(image-Microsoft)-480x270.png) +
+ Syncing passkeys with Microsoft Entra ID
 IT Experts Wed, Dec 31 2025Wed, Dec 31 2025 password, active directory, security, entra, passkey 0
IT Experts Wed, Dec 31 2025Wed, Dec 31 2025 password, active directory, security, entra, passkey 0 -
-480x270.png) +
+ S2D and SAN coexistence in Windows Server failover clustering for Hyper‑V, SQL Server, and file services
 IT Experts Mon, Dec 29 2025Mon, Dec 29 2025 virtualization, windows server, hyper‑v, storage, windows, windows server 2025 0
IT Experts Mon, Dec 29 2025Mon, Dec 29 2025 virtualization, windows server, hyper‑v, storage, windows, windows server 2025 0 -
 +
+ Microsoft to block unauthorized scripts in Entra ID logins with 2026 CSP update
 IT Experts Thu, Dec 18 2025Thu, Dec 18 2025 active directory, security, identity, entra 0
IT Experts Thu, Dec 18 2025Thu, Dec 18 2025 active directory, security, identity, entra 0 -
-480x270.png) +
+ Windows Server 2025 introduces native NVMe support with performance gains of up to 80 percent
 IT Experts Wed, Dec 17 2025Wed, Dec 17 2025 performance, windows server, storage, windows, windows server 2025 0
IT Experts Wed, Dec 17 2025Wed, Dec 17 2025 performance, windows server, storage, windows, windows server 2025 0 -
 +
+ UserLock 13.0: IAM for Active Directory with granular MFA, contextual access controls, and real-time session management
 IT Experts Tue, Dec 16 2025Thu, Dec 18 2025 authentication, active directory, security, windows 0
IT Experts Tue, Dec 16 2025Thu, Dec 18 2025 authentication, active directory, security, windows 0 -
-480x270.png) +
+ New features in Microsoft Entra: WebView2, AI Agents ID, synced passkeys
 IT Experts Mon, Dec 15 2025Mon, Dec 15 2025 active directory, cloud computing, azure, identity, entra 0
IT Experts Mon, Dec 15 2025Mon, Dec 15 2025 active directory, cloud computing, azure, identity, entra 0 -
 +
+ Self-service password reset with SMS in Microsoft Entra External ID
 IT Experts Mon, Dec 15 2025Mon, Dec 15 2025 password, active directory, security, entra 0
IT Experts Mon, Dec 15 2025Mon, Dec 15 2025 password, active directory, security, entra 0 -
 +
+ Microsoft removes WINS after Windows Server 2025
 IT Experts Thu, Nov 27 2025Thu, Nov 27 2025 networking, active directory, security, dns 0
IT Experts Thu, Nov 27 2025Thu, Nov 27 2025 networking, active directory, security, dns 0 -
 +
+ New Windows 11 25H2 Group Policy settings
 IT Experts Thu, Nov 13 2025Mon, Dec 8 2025 group policy, active directory, windows, windows 11 0
IT Experts Thu, Nov 13 2025Mon, Dec 8 2025 group policy, active directory, windows, windows 11 0 -
-480x270.png) +
+ Windows Server 2025 WSUS blocks ESU updates
 IT Experts Fri, Oct 17 2025Mon, Nov 10 2025 patch management, wsus, windows server, security, windows, windows server 2025 0
IT Experts Fri, Oct 17 2025Mon, Nov 10 2025 patch management, wsus, windows server, security, windows, windows server 2025 0 -
 +
+ Install Linux Subsystem for Windows (WSL) on Windows Server 2025
 Markus Elsberger Wed, Oct 15 2025Wed, Oct 15 2025 linux, windows server, windows, windows server 2025, wsl 3
Markus Elsberger Wed, Oct 15 2025Wed, Oct 15 2025 linux, windows server, windows, windows server 2025, wsl 3 -
 +
+ AD replication error 8418: The replication operation failed because of a schema mismatch between the servers involved
 IT Experts Mon, Oct 13 2025Mon, Oct 13 2025 exchange, windows server, active directory, windows, windows server 2025 0
IT Experts Mon, Oct 13 2025Mon, Oct 13 2025 exchange, windows server, active directory, windows, windows server 2025 0 -
 +
+ Remote Desktop credential delegation (SSO) not working after enabling Credential Guard
 Leos Marek Thu, Oct 9 2025Fri, Oct 10 2025 windows server, security, remote desktop services, windows 0
Leos Marek Thu, Oct 9 2025Fri, Oct 10 2025 windows server, security, remote desktop services, windows 0 -
-480x270.png) +
+ Understanding the interaction between Microsoft Defender for Identity and Secure Score
 IT Experts Tue, Oct 7 2025Tue, Oct 7 2025 active directory, security, cloud computing, azure 0
IT Experts Tue, Oct 7 2025Tue, Oct 7 2025 active directory, security, cloud computing, azure 0 -
 +
+ New Administrative Templates (ADMX/ADML) for Windows, Outlook, Word, Excel, and OneNote
 IT Experts Wed, Sep 24 2025Wed, Sep 24 2025 office, group policy, active directory 0
IT Experts Wed, Sep 24 2025Wed, Sep 24 2025 office, group policy, active directory 0 -
 +
+ Migrate a Print Server to Windows Server 2025
 Leos Marek Wed, Sep 17 2025Fri, Nov 14 2025 windows server, windows, windows server 2025 0
Leos Marek Wed, Sep 17 2025Fri, Nov 14 2025 windows server, windows, windows server 2025 0 -
 +
+ MPA Tools: Enhancing Microsoft endpoint management for Windows, Active Directory, Configuration Manager, Intune, and Entra ID
 Brandon Lee Thu, Sep 4 2025Thu, Sep 4 2025 system center, active directory, systems management, configuration manager, windows, intune 0
Brandon Lee Thu, Sep 4 2025Thu, Sep 4 2025 system center, active directory, systems management, configuration manager, windows, intune 0
Tag » Add Computer To Domain Powershell Without Restart
-
Add-Computer (Microsoft.PowerShell.Management)
-
Add New Computer Name To A Domain Without Rebooting? Possible?
-
Powershell Rocks, Rejoin Computers In Domain Without Restart - VGeek
-
Leaving And Rejoining The Domain Without Rebooting (now)
-
Rejoin To Domain After Re-imaging (without Rebooting Twice)?
-
Trust Relationship Rejoin Computers In Domain Without Restart | VGeek
-
Rejoin Computers In Domain Without Restart - RayLin ICT
-
Rejoin A Computer To Domain Without Restart
-
How To Add A Computer To A Domain (GUI And PowerShell)
-
Rejoin A Computer From A Domain In One Easy Step!
-
Powershell Rename PC And Join Domain - Stack Overflow
-
Rename Computer And Join To Domain In One Step With PowerShell
-
How To Add Computers To A Domain Using PowerShell
-
Fix Trust Relationship Failed Issue Without Domain Rejoining



