What Are Email Viruses And How Do You Protect From Them?
Maybe your like
- Home
- Threats and vulnerabilities
- Rahul Awati
- Linda Rosencrance
What is an email virus?
An email virus consists of malicious code distributed in email messages to infect one or more devices. This malicious code can be activated in numerous ways: when the email recipient clicks on an infected link within the message, opens an infected attachment or interacts with the message in some other way.
Email viruses often spread by causing the malicious message to be sent to everyone in the original victim's address book.
Simply put, an email virus is a malicious code or a link to malicious code sent via email. The virus has the ability to replicate itself so it can quickly spread from one device to another. Thus, an email virus can not only infect the victim's computer, but it can also infect the computers of everyone in the victim's address book or those sharing the same network.
There are three primary ways an email virus can infect a victim's email and computer:
- via a phishing email
- included in an attachment
- embedded within the email body
Email viruses often look like executable files with extensions such as the following:
- .exe
- .dll
- .com
- .bat
- .cmd
- .pif
- .scr
- .dot
- .xls
- .xlt
- .docm
How to recognize an email virus
The various types of email viruses present themselves differently, so it's not always possible to recognize when an email message contains a virus.
Some infected emails have subject lines that don't make sense -- e.g., they contain gibberish text or strange special characters -- making them easy to spot. The other header fields and body content of the email may also look peculiar in some way. In other cases, the sender may be unknown to the user, which may raise the user's suspicion.
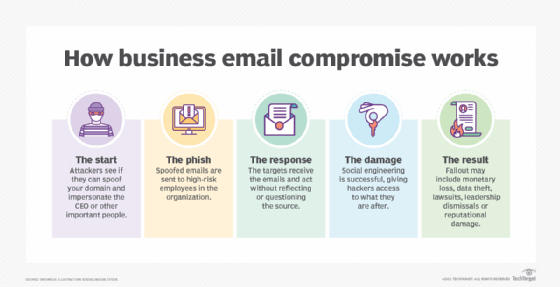
But other email messages containing viruses can be more difficult for recipients to identify. In such cases, the malicious actor may disguise the message so it appears to originate from a trusted and/or known sender. This is particularly true of email phishing campaigns carried out to further business email compromise attacks.
What can an email virus do?
An email virus can wreak all kinds of havoc:
- distribute and execute ransomware attacks;
- enlist the victim's system into a botnet;
- crash the victim's system;
- provide a threat actor with remote access to the victim's device;
- steal the victim's personal data or destroy their files;
- create unwanted pop-ups; or
- add the victim system to a malvertisement.
Email viruses are especially dangerous since they can gather information about the victim -- and their contacts -- without their knowledge. Using such a covert means of attack, an email virus can end up causing massive damage in a short period of time. By the time the victims realize that there is a problem, it's often too late to contain the damage.
Email virus and phishing
Email viruses are often connected with phishing attacks, in which hackers send out malicious messages that look as if they are originated from legitimate, known or trusted sources, such as the following:
- the victim's bank;
- social media;
- internet search sites;
- friends, relatives or co-workers; or
- someone high up in their company, e.g., chief executive officer.
The attacker's goal is to trick the victim into revealing personal and potentially valuable information, such as their address, passwords, credit card number, Social Security number, etc.
Social engineering methods, like spam and malware-filled email messages, are commonly used by threat actors to infect user devices with email viruses and to attack their organization's network.
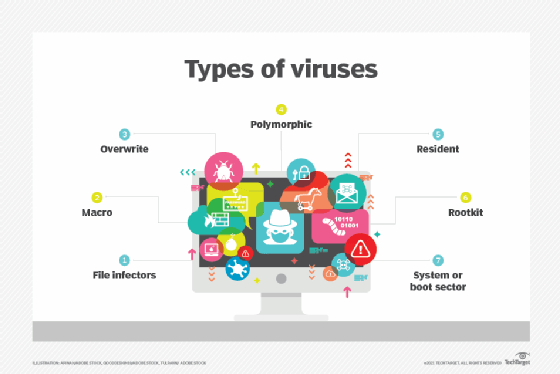
Types of email viruses
Email viruses can take many different forms:
- Email spam. Email spam, also known as unwanted or unsolicited email, usually spreads malware through links in the message. These links, when clicked, often take the victim to a phishing website that steals their data or to other sites hosting malware that further infects their device.
- Boot sector virus. This virus targets the device's master boot record. It can be hard to remove and often requires a full system format, making it one of the most dangerous and persistent types of email viruses.
- Multipartite virus. This virus can simultaneously attack the victim computer's executable files and boot sector. It can also wipe out the hard drive or solid-state storage device. As the virus spreads, it takes up memory, and the user gets multiple pop-up messages advising about low virtual memory. This is a sign the computer is infected with a multipartite virus.
- Resident virus. A resident virus immediately installs itself on the victim's computer as soon as they click on an infected email. Even if the primary virus source is removed, the virus persists in the system and is, therefore, difficult to resolve.
- Virus hoax. Virus hoax messages contain a false warning about a nonexistent threat and often instruct the recipient to take some action, such as forwarding the warning to all their contacts. These messages are a type of socially engineered email virus. One variant builds on the tech support phone scam, in which a malicious actor calls a victim and offers to "help" them with a problem that they purportedly discovered on the victim's computer.
- Macro virus. A macro virus is written in a macro language used by other software programs, especially Microsoft Excel and Microsoft Word. It is transmitted through a phishing email message containing a malicious attachment. As users share the infected documents with others, often by forwarding the email, the virus spreads and infects additional devices.
- Spambot. Spambot programs harvest email addresses to build mailing lists for sending spam. Although they're not usually distributed through email, they are instrumental in gathering valid email addresses that are then used to distribute email viruses.

Examples of well-known email viruses
This rogues' gallery of email viruses were particularly destructive:
- Melissa. Released in 1999, Melissa is one of the oldest email viruses. This fast-spreading macro virus was distributed as an email attachment, which, when opened, disabled many safeguards in Word 97 and Word 2000. Melissa also resent the virus to the first 50 people in each of its victims' address books.
- ILOVEYOU. In May 2000, the fast-spreading ILOVEYOU virus shut down email services in several major enterprises, including Microsoft and Ford Motor Company. In about 10 days, ILOVEYOU affected about 45 million users and caused about $10 billion in damages.
- Mydoom. In early 2004, MyDoom sent spammy junk mail through infected computers and hit several tech companies, including Microsoft and Google, with a distributed denial-of-service attack. It infected 16% to 25% of email messages in 2004.
- Storm Worm Trojan horse. This Trojan horse malware spread through infected attachments in email messages that exploited users' concerns about European storms.
- CryptoLocker ransomware. CryptoLocker, which spread via phishing emails and malicious attachments, encrypted victims' files. The hackers then demanded a ransom from the victims to unlock the files.
How to detect email virus infections
Email viruses have evolved and become more dangerous over time. To combat them, detection methods have evolved as well:
- Signature-based detection. When a new virus variant is discovered, its signature is added to the signature database of the antivirus software. This approach is still in use today. However, it has some limitations that enable threat actors to create advanced viruses that can avoid matching with existing signatures.
- Heuristics. Heuristic analysis involves examining code for suspicious properties to detect previously unknown viruses and new variants of existing viruses.
- Real-time protection. Antivirus and antimalware programs constantly monitor systems for suspicious activity to protect the systems in real time.
- Sandbox detection. This behavior-based detection technique runs programs in a virtual environment and logs their actions to determine if a program is malicious.

How to prevent email virus infections
Email is an indispensable part of the modern worker's life. While it's not possible to stop using email to avoid email viruses, it is possible to take steps to avoid becoming a victim of such attacks.
The most important preventive tool is antivirus software. A trusted antivirus app that's updated with the latest virus definitions can go a long way toward thwarting email viruses.
Other ways to prevent an email virus from infecting a device or network include the following:
- Scan all email attachments for malware.
- Be careful about opening attachments from unknown sources.
- Avoid opening executable files included as attachments.
- Regularly update and patch mail clients, web browsers and operating systems.
- Never click on links in the body of email messages.
- Double-check the sender's name to confirm that an email is from a legitimate source.
- Watch for other signs that may indicate phishing emails, such as obvious grammatical errors, suspicious attachments, strange domain names, etc.
Continue Reading About email virus
- Explore 5 business email compromise examples to learn from
- Games, not shame: Why security awareness training needs a makeover
- How to send secure email attachments
- How to choose the right email security service for your organization
- Detecting and Combating Malicious Email
Related Terms
What is a cloud access security broker (CASB)? A cloud access security broker (CASB) is a software tool or service that sits between an organization's on-premises ... See complete definition What is a stealth virus and how does it work? A stealth virus is a computer virus that uses various mechanisms to avoid detection by antivirus software. See complete definition What is antivirus software? Antivirus software (antivirus program) is a security program designed to prevent, detect, search and remove viruses and other ... See complete definitionDig Deeper on Threats and vulnerabilities
-
![]()
Malware vs. ransomware: What's the difference?
 By: Phil Sweeney
By: Phil Sweeney -
![]()
12 common types of malware attacks and how to prevent them
 By: Sharon Shea
By: Sharon Shea -
![]()
What is malware? Prevention, detection and how attacks work
 By: Kinza Yasar
By: Kinza Yasar -
![]()
virus (computer virus)
 By: Robert Sheldon
By: Robert Sheldon
- Using Member Engagement to Balance Personalization, Participation –Zelis Healthcare
- Securing Healthcare: Overcoming Cyber Threats Amid Limited Resources –Commvault + Microsoft
- See More
- 6 Ways to Keep Your Endpoint Devices Secure –Sentinel Labs, Inc.
- Recognizing serious diseases spread by mosquitoes –XtelligentMedia Healthcare
- Networking
- CIO
- Enterprise Desktop
- Cloud Computing
- Computer Weekly
- 5 principles of change management in networking
Network change management includes five principles, including risk analysis and peer review. These best practices can help ...
- How network efficiency advances ESG goals
From SDN to green electricity, network optimization plays a critical role in helping enterprises reduce emissions, cut costs and ...
- How to build a private 5G network architecture
A private 5G network can provide organizations with a powerful new option for their wireless environments. Here are the major ...
- What CIOs can learn from Marc Benioff's ICE joke
Marc Benioff's ICE agent joke at a Salesforce all-hands meeting puts spotlight on IT system and operational risks with ...
- AI workforce training: How BDO USA trains its employees
Getting employees comfortable with AI is tough for CIOs. BDO USA uses AI ambassadors, tailored training and a virtual escape room...
- AI transformation is inevitable but requires change management
Enterprises are split on AI adoption speed. While some take an aggressive workforce overhaul, others preach more careful ...
- The promise and concern around end-user AI second brains
Human-delegated AI agents and "second brains" could transform knowledge work, but only if IT can balance governance, data ...
- How Windows 11 Safe Mode works and when to use it
Windows 11 Safe Mode gives IT leaders a reliable way to diagnose failures, restore access to broken systems and strengthen ...
- How Windows 11 Print Management can fix printer issues
IT admins can use Print Management in Windows 11 to manage all printers connected to a device, troubleshoot problems and restart ...
- Top enterprise hybrid cloud management tools to review
The techniques used to build hybrid cloud architectures have come a long way, but managing these environments long term is plenty...
- GenAI drives $119B cloud revenue in Q4
Q4 cloud infrastructure service revenues reach $119.1 billion, bringing the 2025 total to $419 billion. See how much market share...
- Cloud infrastructure suffers AI growing pains
Will $5 trillion in AI infrastructure investment be enough? Cloud providers facing that question must also yield a return, ...
- Scattered data, cloud transfers creating challenges in enterprise AI
The cost, speed, and governance of moving petabytes of across multi and hybrid cloud environments is becoming a challenge for ...
- National Grid, Nebius and Emerald hail datacentre power throttling
In a UK-first trial, Emerald AI acts as intelligence in datacentre energy management to throttle demand at peak loads, including ...
- Interview: Wolf & Badger CEO George Graham on getting ‘hands-on’ with AI
From continually exploring the potential of artificial intelligence to actually building and introducing AI-enabled systems for ...
Tag » How To Send Virus Through Email
-
Can I Send A Virus Through Emails? - Quora
-
Email Virus | Top 3 Ways An Email Virus Infects Computers - Comodo
-
5 Tricks Used In Emails To Deliver Malware - Gatefy
-
How To Send A Trojan Virus Through Email –
-
Virus Basics | CISA - US-CERT
-
How To Send A Virus Via Email...... - Go4Expert
-
I Want To Send A Virus/malware File To A Scammer. - Reddit
-
Can I Get A Virus By Replying To An Email? - Paubox
-
Complete Guide To Email Viruses & Best Practices To Avoid Infections
-
Email With A Virus Payload - YouTube
-
How To Make A Virus And Send It In A Email EASY! - YouTube
-
How To Make A Fake Virus And Send It By Email - YouTube
-
Can You Get A Virus From Opening An Email? - Guardian Digital
-
Send Virus Through Email 2022



