What Is A Domain Controller? - TechTarget
Maybe your like
- Home
- Microsoft identity and access management
- Gavin Wright
- Peter Loshin, Former Senior Technology Editor
A domain controller is a server that processes authentication requests from users and computers within a computer domain. Domain controllers are most commonly used in Windows Active Directory (AD) domains, but are also used with other types of identity management systems.
Domain controllers maintain directory service information for their domains, including users, authentication credentials and enterprise security policies.
What are the main functions of a domain controller?
Domain controllers restrict access to domain resources by authenticating user identity through login credentials and preventing unauthorized access to those resources.

Domain controllers apply security policies to requests for access to domain resources. For example, in a Windows AD domain, the domain controller draws authentication information for user accounts from AD.
A domain controller can operate as a single system, but is usually implemented in clusters for improved reliability and availability. For domain controllers running under Windows AD, each cluster comprises a primary domain controller and one or more backup domain controllers.
Insecure sites can use a read-only domain controller to speed up authentication. In Unix and Linux environments, domain controllers can manage Lightweight Directory Access Protocol domains.
Why is securing a domain controller important?
Domain controllers authorize all domain access, blocking unauthorized access to domain resources while allowing users access to authorized directory services. They also store many of the secrets that a domain uses to protect users and data. If someone gains unauthorized access to a domain controller, they can quickly gain access to all the data stored on the network, making domain controllers a primary target for attackers.
It is important to harden the domain controller with additional security mechanisms, such as the following:
- Firewalls.
- Isolated networks.
- Security protocols and encryption to protect stored data and data in transit.
- Restricted use of insecure protocols, such as Remote Desktop Protocol, on controllers.
- Deployment in a physically restricted location for security.
- Expedited patch and configuration management.
- Blocking internet access for domain controllers.
- Dedicated administrator accounts.
How are domain controllers set up in Active Directory?
The domain controller is the central server in a Windows AD domain. Domain controllers are servers that can use AD to respond to authentication requests.
Experts advise against relying on a single domain controller, even for smaller organizations. Best practices call for one primary domain controller and at least one backup domain controller to avoid downtime caused by system unavailability.
Domain controllers can be deployed on physical servers, running as virtual machines (VMs) or as part of a cloud directory service. It is best practice to deploy each domain controller on a standalone server. This includes virtual domain controllers, which should run on VMs running on different physical hosts. This minimizes the possibility of a compromise on another machine affecting the domain controller.
Setting up an AD domain controller includes the following steps:
- Domain assessment. The first step in setting up a domain controller is to assess the domain in which the controller will be set up. This assessment includes determining what types of domain controllers are needed, where they will be located and how they interoperate with existing systems in the domain.
- New deployment or addition. Whether planning for a new deployment of AD domain controllers or adding a new controller for an existing domain, determine the domain controller location as well as the resources needed to run the centralized domain controller and any virtual domain controllers.
- Security by design. It's imperative to secure a domain controller from internal or external attacks. The domain controller architecture must also be designed to withstand service disruptions such as loss of connectivity, loss of power or system failures.
Specifics for setting up and configuring AD domain controllers vary depending on the version of Windows Server used on the domain.
Other domain controller implementation options
The following options are available when setting up a domain controller with AD:
- Domain Name System server. The DNS domain controller can be configured to function as a DNS server. The DNS service provides the mapping of the computer name to its associated Internet Protocol address.
- Global catalog capabilities. The domain controller can be configured to use the global catalog, which enables the controller to return AD information about any object in the organization forest, regardless of whether the object is in the same domain as the domain controller. This is useful for large enterprises with multiple AD domains.
- Read-only domain controller. Domain controllers used in branch offices or in other circumstances where network connectivity is limited can be configured as read-only.
- Directory Services Restore Mode. DSRM enables emergency maintenance, including restoring backups, on the domain controller. A DSRM password must be configured in advance.
- Certificate services. Certificate services enable a domain controller to issue and authenticate certificates for authentication and encryption.
- Group policy. Domain controllers host AD group policies, which can be used to enforce security settings on domain member servers and clients.
- Distributed file system. DFS uses multiple file servers to host shared files. The servers can automatically replicate files and hide the underlying server structure from end users.
The same server can host other Windows services, such as a file share or print server. However, this is not recommended, as these other services could compromise the domain controller.
What are the benefits of domain controllers?
Domain controller benefits include the following:
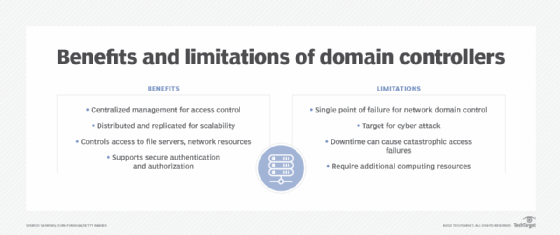
- Centralized management of authentication enables organizations to authenticate all access requests with a single set of credentials.
- Enforcement of security policies, such as password age, complexity and lockout, helps to prevent unauthorized access across an enterprise.
- Access to file servers, email and other network resources through domain controllers provides seamless integration with Microsoft AD.
- Support for secured authentication and transport protocols in domain controllers improves authentication process security.
What are the limitations of domain controllers?
Some domain controller limitations include the following:
- Domain controllers can be a single point of failure for network domain control.
- Because they control access to the entire network, domain controllers are a target for cyberattacks. Successfully hacking a domain controller could give the attacker access to all domain network resources as well as authentication credentials for all users in the domain.
- Networks that use domain controllers for authentication and access security are dependent on them. To reduce the risk of downtime, controllers can be deployed in clusters.
- Domain controllers require additional infrastructure and security mechanisms.
Alternatives to domain controllers
Domain controllers have historically been the center of an organization's identity and access management. Still, they don't natively support many of the advanced features that are part of a modern environment.
Traditional castle-and-moat-style networks have given way to zero-trust networks. Simple passwords are being replaced by passkeys and two-factor authentication.
Microsoft Entra ID is a cloud-based identity manager. It is part of Microsoft's Azure cloud platform. Entra ID is designed to be secure from the start and support modern authentication.
Federated identities enable one authentication service to be used for other services. For example, a Google account can be used to sign in to an accounting website.
Amazon Web Services Directory Service is a managed AD service offered by Amazon. It hosts an AD environment in AWS.
Hybrid domain controllers
Hybrid cloud environments, which combine on-premises and cloud-based infrastructure, are becoming more prevalent. Domain controllers can be configured with tools to sync accounts and passwords with a cloud identity provider, such as Microsoft Entra ID. This enables users to have a single set of credentials that works for both on-premises and internet resources.
With hybrid deployments, a single management interface can be used to control access to all resources. Hybrid deployments are a good option for organizations that are not ready to move entirely to the cloud, but that use some online resources.
Account sync can be set up to be one-way or two-way. In a one-way sync, the on-premises information is sent to the cloud provider. Typically, only password hashes are synced; this prevents the possibility of the passwords being compromised, but could also prevent some features from working, such as self-service password resets. In a two-way sync, the online service can change the on-premises accounts.
Domain controllers are fundamental to securing unauthorized access to an organization's domains. Learn how to securely set up and deploy a Windows Server 2022 domain controller. Also, check out this Windows Server 2022 security hardening guide for admins.
Continue Reading About What is a domain controller?
- What are the Microsoft Entra ID benefits for on-prem admins?
- How to edit a Domain Group Policy for a Windows desktop
- Using Microsoft AD Explorer for common admin tasks
- How to transfer FSMO roles with PowerShell
- How to disable removable media access with Group Policy
Related Terms
What is a brute-force attack? A brute-force attack is a trial-and-error hacking method cybercriminals use to decode login information and encryption keys to ... See complete definition What is a passkey? A passkey is an alternative user authentication method that eliminates the need for usernames and passwords. See complete definition What is Universal 2nd Factor (U2F)? Universal 2nd Factor (U2F) is a physical device that can act as a form of authentication for an account. See complete definitionDig Deeper on Microsoft identity and access management
-
![]()
How to join Linux to an Active Directory domain
 By: Stuart Burns
By: Stuart Burns -
![]()
What is Active Directory (AD)?
 By: Rahul Awati
By: Rahul Awati -
![]()
What is Active Directory Domain (AD Domain)?
 By: Rahul Awati
By: Rahul Awati -
![]()
Deploy a read-only domain controller for security, speed
 By: Damon Garn
By: Damon Garn
- Best Practices: Preparing for the Inevitable Healthcare Cyberattack –Commvault + Microsoft
- Improving Operational Efficiencies: 4 Success Stories in Digital Transformation –Dell Technologies
- See More
- Atlassian Admin Security Guide –Atlassian
- Identifying Tier 0 with Active Roles –One Identity
- Cloud Computing
- Enterprise Desktop
- Virtual Desktop
- GenAI drives $119B cloud revenue in Q4
Q4 cloud infrastructure service revenues reach $119.1 billion, bringing the 2025 total to $419 billion. See how much market share...
- Cloud infrastructure suffers AI growing pains
Will $5 trillion in AI infrastructure investment be enough? Cloud providers facing that question must also yield a return, ...
- 8 reasons why IT leaders are embracing cloud repatriation
As IT leaders aggressively re-allocate capital to fund new AI initiatives, repatriation offers both savings and greater control, ...
- How Windows 11 Safe Mode works and when to use it
Windows 11 Safe Mode gives IT leaders a reliable way to diagnose failures, restore access to broken systems and strengthen ...
- How Windows 11 Print Management can fix printer issues
IT admins can use Print Management in Windows 11 to manage all printers connected to a device, troubleshoot problems and restart ...
- How to migrate applications to Windows 11
As Windows 10 support ends, organizations must plan Windows 11 migrations carefully. Assess apps, data and device configurations ...
- How to configure the Remote Desktop Users group in Windows
Managing the Remote Desktop Users group is essential for secure Windows access. IT teams should know how to configure it properly...
- How to enable and manage Windows 11 Hyper-V
Hyper-V virtual machines have many use cases in enterprise IT. Windows administrators should follow these steps to create new VMs...
- Understanding the DaaS options for Macs
When people discuss desktop as a service, it is usually in the context of Windows desktops. For macOS, however, implementing DaaS...
Tag » Ad Dc Windows Server 2016
-
Active Directory Domain Creation In Windows Server 2016 (Standard)
-
Active Directory Domain Services In Windows Server 2016
-
Active Directory Domain Services Overview - Microsoft Docs
-
Install Active Directory Domain Services (Level 100) - Microsoft Docs
-
Step-by-Step Guide To Setup Active Directory On Windows Server 2016
-
Setup Active Directory On Windows Server 2016 - PC
-
Windows Server 2016 How To Install An Active Directory ... - YouTube
-
How To Setup A Domain Controller - ManageEngine
-
What Is Active Directory? A Step-by-step Tutorial - Comparitech
-
Active Directory - Wikipedia
-
Windows Server 2016 - Setup Local Domain Controller | Tutorials
-
Install And Configure Active Directory Domain Services In Windows ...
-
ActiveDirectory Domain Controller For Windows 2016 - Amazon AWS
-
Step-By-Step: Manually Removing A Domain Controller Server



