What Is Anti-replay Protocol And How Does It Work? - TechTarget
Maybe your like
- Home
- Network infrastructure
 By
By - Rahul Awati
What is anti-replay protocol?
The anti-replay protocol provides Internet Protocol (IP) packet-level security by making it impossible for a hacker to intercept message packets and insert changed packets into the data stream between a source computer and a destination computer. By detecting packets that match the sequence numbers of those that have already arrived, the mechanism helps ensure that invalid packets are discarded and communication integrity is maintained.
This anti-replay protocol is a subprotocol of the Internet Engineering Task Force's IP Security (IPsec) standard suite of protocols. The two main protocols under IPsec -- Encapsulating Security Payload (ESP) and Authentication Header (AH) -- both use anti-replay protection.
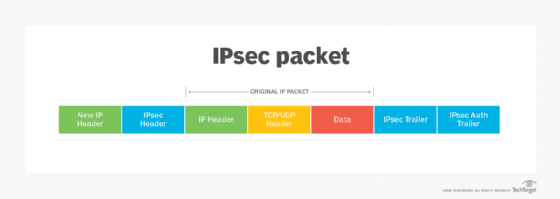
What is a replay attack?
A replay attack occurs when threat actors eavesdrop on a secure network to intercept and record its legitimate communications or data transmissions. They then either delay, resend or repeat this data in order to do the following:
- impersonate a valid user;
- misdirect the receiver into doing something they might not have done otherwise; or
- disrupt legitimate connections.
The goal of a replay attack is to subvert security and cause some kind of negative impact on authorized users and connections.
Real-world example of a replay attack
An employee requests a financial transfer by sending an encrypted message to an authorized person within the company. This could be someone like the financial administrator or a senior accountant.
A hacker captures the message and resends it to the same target recipient. Because the message remains authentic -- it has not been altered -- is correctly encrypted and has simply been resent, it looks legitimate to the recipient.
As a result, receivers may honor the request for the money transfer, unaware that they -- and their organization -- have just been swindled out of a large sum of money.
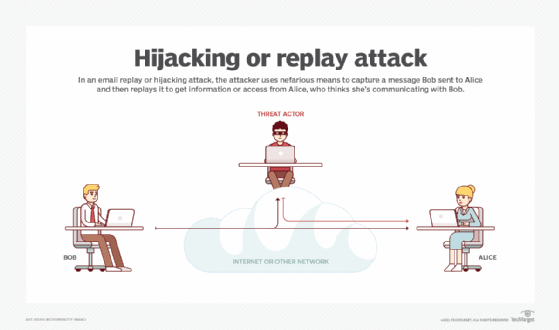
How does the anti-replay protocol work?
The answer to preventing replay attacks is encrypting messages and including a key. IPsec provides anti-replay protection against attackers who could potentially intercept, duplicate or resend encrypted packets.
The mechanism uses a unidirectional security association to establish a secure connection between the source and destination nodes in the network and check whether a received message is a replayed message. It works by assigning a monotonically increasing sequence number to each encrypted packet and then keeping track of the sequence numbers as packets arrive at the destination.
At the outset, the counters of both the source and destination are initialized at 0. The first sent packet has a sequence number of 1, the second packet is numbered 2 and so on. Each time a packet is sent, the receiver verifies that the number is not that of a previously sent packet. If the next packet has a lower number than the previous packet, the destination will drop the packet. If the number is larger, it keeps the packet.
Also, when a replayed packet is detected, the anti-replay protocol generates an error message. It also discards this packet and logs the event with entry identifiers, such as the date/time received, source address, destination address and sequence number.
Enhancing the anti-replay protocol
The anti-replay protocol is designed to overcome adversaries that can insert only replayed messages in the message stream. However, this protocol can be enhanced to overcome bad actors that can potentially insert any message into the message stream.
Here's how it works: A shared secret is provided to both the source and destination computer. The adversary does not know this shared secret. Each message sent by the source consists of three elements: the message sequence number, the message text and the message digest.
Before the destination receives the message, the protocol verifies if the message digest meets a specific value. If a bad actor inserts a message in the message stream between the source and destination, the protocol checks whether the message has been sent earlier by the source or if the digest does not meet the predetermined value.
In either case, the destination discards the message.
What is the AH protocol?
The IPsec AH protocol provides user authentication and integrity protection for packet headers and data. It may also provide replay protection and access protection but cannot encrypt any portion of packets. AH functions in two modes:
- Transport
- does not alter the original IP header or create a new IP header
- usually used in host-to-host architectures
- Tunnel
- creates a new IP header for each packet
What is the ESP protocol?
ESP provides encryption for packet payload data and authentication to provide integrity protection -- but not for the outermost IP header and protection services. Like the AH protocol, ESP also functions in the transport and tunnel modes. In the latter scenario, it creates a new IP header -- for each packet -- which lists the endpoints of the ESP tunnel as the packet's source and destination.
This feature makes ESP ideal for virtual private network architecture models.
Continue Reading About anti-replay protocol
- What are the top secure data transmission methods?
- Best practices for VPN traffic monitoring
- How to calculate a subnet mask from hosts and subnets
- How to secure REST API endpoints for cloud applications URL
- How does IP hijacking work and how can it be prevented?
Related Terms
What is 5G? Fifth-generation wireless or 5G is a global standard and technology for wireless and telecommunications networks. See complete definition What is a small cell in wireless networks? A small cell is a type of low-power cellular radio access point or base station that provides wireless service within a limited ... See complete definition What is millimeter wave (mmWave)? Millimeter wave (mmWave) is a range of electromagnetic frequencies that exist between microwaves and infrared light. See complete definitionDig Deeper on Network infrastructure
-
![]()
What is a network packet?
 By: Rahul Awati
By: Rahul Awati -
![]()
What is a protocol data unit (PDU)?
 By: Peter Loshin
By: Peter Loshin -
![]()
What is Internet Key Exchange (IKE)?
 By: Gavin Wright
By: Gavin Wright -
![]()
What is IPsec (Internet Protocol Security)?
 By: Katie Terrell Hanna
By: Katie Terrell Hanna
- Is Your EHR the Problem? –Greenway Health
- Using Member Engagement to Balance Personalization, Participation –Zelis Healthcare
- See More
- The 5 Different Types of Firewalls Explained –TechTarget
- Unified Communication: “It should work as easily as a telephone call!” –TechTarget ComputerWeekly.com
- Unified Communications
- Mobile Computing
- Data Center
- IT Channel
- AI rewrites ROI for next-generation video conferencing
As AI drives the advancement of video systems, IT leaders must reevaluate infrastructure needs and develop new ROI frameworks ...
- How UCaaS solves the cost of poor communication
Legacy UC systems are no longer enough to support today's employee communication needs. Explore why migrating to UCaaS is key to ...
- Enterprise AR and VR: Building the UC business case
Enterprise VR and AR enable immersive collaboration, virtual training and improved CX, but also require careful consideration of ...
- Android vs. iPhone: Which one is more secure?
Apple has built a reputation for strong device security, but reputation alone can't protect corporate data. While iOS and Android...
- How to fix an iPhone Personal Hotspot that's not working
Connectivity issues, misconfigured settings and human error can all cause mobile hotspot problems. IT must know how to avoid and ...
- How to set up kiosk mode for iPad and other OSes
Tablet-based kiosks have become an increasingly popular tool for customer self-service. Organizations managing multiple kiosks ...
- Data center safety checklist: 10 best practices to follow
Data center facilities pose various risks to those who operate them. Here are 10 best practices to follow when implementing data ...
- Space-based data centers: Edge computing in space
Space-based data centers, which enable edge computing in space, have the potential to revolutionize data management by reducing ...
- Enhance operations with decentralized data centers
Decentralized data centers enhance scalability, reduce latency and improve data compliance, offering a strategic shift for ...
- Geography, skills drive IT Services M&A for Presidio, Accenture
Presidio has acquired transACT Technology Solutions, a digital transformation specialist based in the United Kingdom, while ...
- Consultants, SIs back AWS agentic AI marketplace launch
Accenture, Cognizant and Deloitte are among the partners with offerings on AWS' AI Agents and Tools marketplace, which is ...
- Partners begin to target agentic AI marketplace platforms
Cloud marketplaces are emerging as key venues for adoption of AI agents. Consultants and integrators aim to offer the technology ...
Tag » How Does Ipsec Prevent Replay Attacks
-
IPSec - Internet Protocol Security
-
Protection Mechanisms (IPsec And IKE Administration Guide)
-
IPsec Protection Mechanisms - Securing The Network In Oracle ...
-
Configuring IPsec Anti-replay
-
Anti-replay - Wikipedia
-
Using ESP To Prevent Replay Attacks | Enterprise Networking Planet
-
What Is A Replay Attack And How To Prevent It - Kaspersky
-
Troubleshoot IPsec Anti-Replay Check Failures - Cisco
-
Replay Protection - An Overview | ScienceDirect Topics
-
Anti-replay Protection - Magic WAN - Cloudflare Docs
-
[PDF] IPSec And IKE
-
How Can IPsec Protects The Network? [Solved] (2022) - Cryptocoached
-
Theory - The Official IPsec Howto For Linux
-
What Is IPSec? | IT PRO



