What Is Cyberstalking And How To Prevent It? - TechTarget
Maybe your like
How to guard against cyberstalking
Individuals can guard against cyberstalking without losing their online independence. One strategy is to stay as anonymous as possible. Of course, complete anonymity is almost impossible on the internet nowadays, so the next best thing is to keep a low profile, especially on social media.
Rather than having an identifiable and traceable online presence, use nicknames and/or gender-neutral names when possible. Avoid posting personal details, such as your email address, home address, phone number or workplace details, online, where anyone can easily access them and use them to cyberstalk. Also, guard photographs, and make sure all private information, like vacation plans, photos and posts, are visible only to trusted individuals.
Use a primary email account only for communicating with known/trusted people and set up an anonymous email account for all other communications. Install email spam filters to minimize spam and the possibility of email-based phishing or cyberstalking attacks.
Other ways to guard against cyberstalking include the following:
- Update all software to prevent information leaks.
- Mask your Internet Protocol address with a virtual private network, i.e., VPN.
- Strengthen privacy settings on social media.
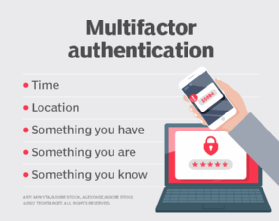
- Strengthen all devices with strong passwords or, better, use multifactor authentication.
- Avoid using public Wi-Fi networks.
- Send private information via private messages, not by posting on public forums.
- Safeguard mobile devices by using password protection and never leave devices unattended.
- Disable geolocation settings on devices;
- Install antivirus software on devices to detect malicious software.
- Always log out of all accounts at the end of a session.
- Beware of installing apps that ask to access your personal information.
Tag » How To Report Cyber Stalking
-
Cyberstalking
-
Cyber Crime — FBI
-
How To Report Cyber Stalking & Protect Yourself [97% Success]
-
What To Do If You Are Being Stalked - The Cyber Helpline
-
Cyber Harassment Resources - Internet Law Center
-
Cyberstalking | ESafety Commissioner
-
Where To Report Online Abuse & Cyberstalking - Endtab
-
What Is Cyberstalking And How To Stop It - Avast
-
What Is Cyberstalking? - Verywell Mind
-
Steps To Reporting Cyber-stalking In India - Serein
-
What Cyberstalking Is And How To Prevent It - Tripwire
-
[PDF] Protection From Cyberstalking: Basic Advice
-
What Is Cyberstalking? How To Help Protect Yourself Against It - Norton
-
How To File A Cyberstalking Complaint - IPleaders