What Is Network Intrusion Protection System (NIPS)? - TechTarget
Maybe your like
- Home
- Security management
 By
By - Paul Kirvan
What is a network intrusion protection system (NIPS)?
A network intrusion protection system (NIPS) is an umbrella term for a combination of hardware and software systems that protect computer networks from unauthorized access and malicious activity. A NIPS helps organizations detect and respond to potential threats in real time, maintaining the integrity and confidentiality of data.
These systems are placed inline with the flow of network traffic, where they examine network packets, protocols and patterns to identify suspicious behavior, such as unauthorized access attempts, malware infections and data breaches. A NIPS detects problems and alerts administrators to potential issues. In doing so, it plays a crucial role in minimizing the impact of cyber attacks and fortifying network defenses.
NIPS hardware often consists of a dedicated network intrusion detection system (NIDS) device, an intrusion prevention system (IPS) or something that functions as a combination of the two, such as an intrusion prevention and detection system. A NIDS detects intrusions, while an IPS proactively stops attacks by following preestablished rules to prevent them.
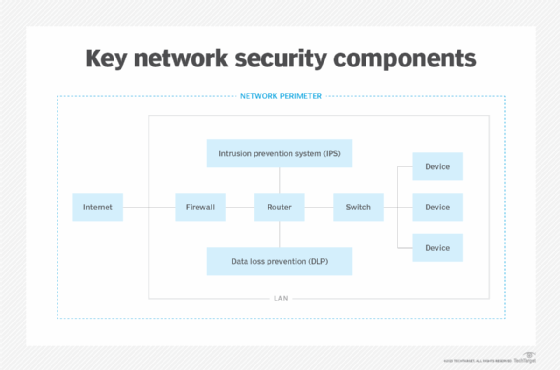
How does a NIPS work?
The software components of a NIPS consist of firewall, sniffer, antimalware and antivirus tools, along with dashboards and data visualization tools. These components work together to continually monitor an organization's computer networks and network perimeters for abnormal traffic patterns and malicious traffic.
Once an anomaly is discovered, the NIPS alerts system administrators to significant events and might even automatically stop potential intrusions. A NIPS uses the following techniques for screening data for anomalies:
- Signature-based detection. The NIPS scans and analyzes data for patterns or signatures of known malware. It regularly updates its database of known signatures and rules to maximize its effectiveness.
- Anomaly-based detection. The NIPS monitors for suspicious or unfamiliar network traffic patterns by using network behavior analysis to sample network activity and regularly compare those samples to a baseline standard. This technique also requires consistent updates to the database of rules and patterns, though newer systems are using artificial intelligence and machine learning to streamline these processes.
- Policy-based detection. Network administrators set specific network security policies and create rules tied to them. Network traffic is monitored for adherence to those policies and rules, and traffic patterns that go against them trigger a response from the system.
A NIPS might use a honeypot or decoy system to attract attackers. Once it detects an anomaly, it takes several actions in quick succession, such as the following:
- Drops suspicious packets.
- Blocks IP addresses from suspicious traffic.
- Quarantines suspicious code for further analysis.
- Notifies network security administrators.
- Generates event logs.
- Revises rules for firewalls and other devices.
- Resets all network connections.
A NIPS is different from a host-based intrusion prevention system, or HIPS, which gets installed at an endpoint and only monitors inbound and outbound traffic for that device. It also differs from a wireless intrusion prevention system, or WIPS, which monitors wireless networks for intrusions.
Why is a NIPS important?
Spyware, distributed-denial-of-service (DDOS) attacks, phishing, viruses, ransomware and other malware attacks continue to grow in frequency. Intrusion protection systems are part of the layered cybersecurity systems networks need.
Some form of a NIPS is vital for any computer network that's at risk of access by unauthorized persons. Computers holding sensitive data always require protection against advanced threats, but even seemingly insignificant networks can be hijacked for use in malware attacks.
In addition to the attack detection and prevention, a NIPS provides documentation demonstrating compliance with various regulations. Organizations need such documentation when conducting security audits.
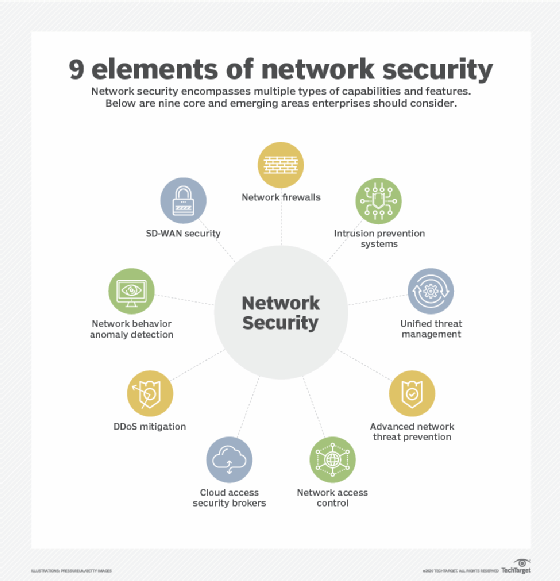
Benefits and challenges of a NIPS
NIPS technology provides organizations with the following advantages:
- Reduces the likelihood of cyber attacks and the issues that come with them.
- Increases threat protection and network visibility.
- Facilitates anomaly analysis.
- Automates network activity monitoring.
- Notifies administrators about any threats or anomalies.
- Makes information readily available to admins.
However, these systems have some challenges, such as the following:
- These systems must be regularly reviewed and updated to ensure their rules and analytical tools remain up to date.
- Insufficient network bandwidth and capacity can result in slower applications while the NIPS operates.
- They can generate false positives that might unnecessarily deny service to users.
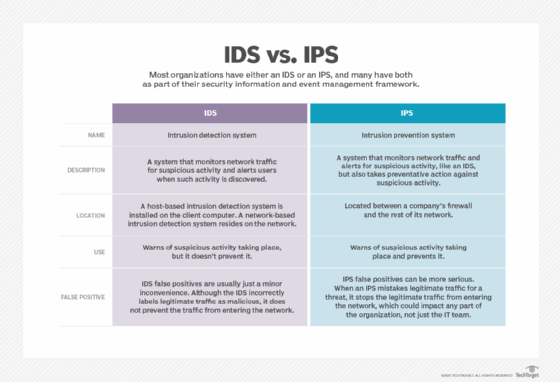
IDS vs. IPS: Which is better?
An IDS identifies and highlights suspicious activity and reports it to network administrators. The admins then must address the anomaly.
An IPS both detects anomalies andtakes action to block them from causing harm to networks and systems. This makes an IPS -- and, by extension, a NIPS -- the preferred approach.
What's the difference between a firewall and a NIPS?
Firewalls and network intrusion protection systems are both key components of network security systems. Nevertheless, there are distinct differences between a NIPS and firewall. They serve different purposes and complement each other in comprehensive network security strategies, such as unified threat management and next-generation firewall systems.
Firewall
Firewalls act as the first line of defense, providing a barrier between an organization's internal network and the external internet. They examine incoming and outgoing network traffic based on predefined rules and policies. They also monitor and control traffic flow, allowing and blocking access based on specified criteria.
Firewalls can be implemented at various levels, such as on networks, applications and even individual devices. They're designed to protect against unauthorized access, DDOS attacks, malware and other threats by filtering and inspecting packets. By analyzing packet headers and content, firewalls can enforce security policies and prevent malicious activities from entering or leaving a network.
Network intrusion protection system
A NIPS is a more advanced security approach to detecting and preventing network intrusions that goes beyond the capabilities of a firewall. A NIPS focuses on detecting and preventing network intrusions in real time. It uses techniques like signature detection, anomaly detection and behavior analysis detection methods to identify malicious activities within the network.
A NIPS monitors network traffic continuously, looking for patterns or anomalies that may indicate an attack or unauthorized access. When a potential threat is detected, the system takes immediate action to block the IP addresses of questionable traffic or otherwise mitigate the attack, preventing further damage.
Learn more about incident response to effectively detect, manage and prevent cyber attacks in the enterprise.
Continue Reading About network intrusion protection system (NIPS)
- The ultimate guide to cybersecurity planning for businesses
- 13 incident response best practices for your organization
- Incident management vs. incident response explained
- Unpack the use of AI in cybersecurity, plus pros and cons
- Next-generation firewall comparison based on company needs
Related Terms
What is counterintelligence? Counterintelligence (CI) is the information gathered and actions taken to identify and protect against an adversary's knowledge ... See complete definition What is digital trust? Digital trust is the confidence users have in the ability of people, technology and processes to create a secure digital ... See complete definition What is identity and access management? Guide to IAM No longer just a good idea, IAM is a crucial piece of the cybersecurity puzzle. It's how an organization regulates access to ... See complete definitionNew & Updated Definitions
- What is 5G New Radio (5G NR)?
5G New Radio, or 5G NR, is a globally accepted standard that delivers more responsive mobile experiences for a wide range of applications over fifth-generation wireless (5G) networks. See More.
- What is multi-access edge computing? Benefits and use cases
- What is 5G?
- What is a small cell in wireless networks?
- What is 6G? Overview of 6G networks & technology
- phase-locked loop (PLL)
- What is identity and access management? Guide to IAM
- What are AI agents? Types and examples
- What is time-sensitive networking (TSN) via 5G?
- Networking
- Security
- CIO
- HR Software
- Customer Experience
- What is multi-access edge computing? Benefits and use cases
Multi-access edge computing (MEC) is a network architecture concept that brings cloud computing capabilities and IT services ...
- What is 5G?
Fifth-generation wireless or 5G is a global standard and technology for wireless and telecommunications networks.
- What is a small cell in wireless networks?
A small cell is a type of low-power cellular radio access point or base station that provides wireless service within a limited ...
- What is identity and access management? Guide to IAM
No longer just a good idea, IAM is a crucial piece of the cybersecurity puzzle. It's how an organization regulates access to ...
- What is data masking?
Data masking is a security technique that modifies sensitive data in a data set so it can be used safely in a non-production ...
- What is antivirus software?
Antivirus software (antivirus program) is a security program designed to prevent, detect, search and remove viruses and other ...
- What is a chief data officer (CDO)?
A chief data officer (CDO) in many organizations is a C-level executive whose position has evolved into a range of strategic data...
- What is user-generated content?
User-generated content (UGC) is published information that an unpaid contributor provides to a website.
- What is business process outsourcing (BPO)?
Business process outsourcing (BPO) is a business practice in which an organization contracts with an external service provider to...
- What is compensation management?
Compensation management is the discipline and process for determining employees' appropriate pay, incentives, rewards, bonuses ...
- What is HR technology (human resources tech)?
HR technology (human resources tech) refers to the hardware and software that support an organization's human resource management...
- What is core HR (core human resources)?
Core HR (core human resources) is an umbrella term that refers to the essential, mandatory and fundamental tasks and functions of...
- What are virtual agents and how are they being used?
A virtual agent is an AI-powered software application or service that interacts with humans or other digital systems in a ...
- Customer acquisition cost (CAC): How to calculate and reduce it
Customer acquisition cost (CAC) is the cost associated with convincing a consumer to buy your product or service, including ...
- What is direct marketing?
Direct marketing is a type of advertising campaign that seeks to elicit an action (such as an order, a visit to a store or ...
Tag » What Is Nip In Networking
-
NIP Networking Abbreviation Meaning - All Acronyms
-
What Is Network-based Intrusion Prevention System (NIPS)?
-
Network Intrusion Protection System (NIPS) Protects Confidentiality ...
-
NIP Definition: Network Implementation Plan - Abbreviation Finder
-
Network-Based Intrusion Prevention - CyberHoot
-
Network Intelligent Protection (NIP) System Reviews - Gartner
-
Network Intrusion Protection System (NIPS) Definition - NordVPN
-
What Does NIP Mean In Networking?
-
What Is A Network Intrusion Prevention System?
-
Hillstone Network Intrusion And Prevention System (NIPS)
-
Network Based Intrusion Detection System
-
What Does NIP Mean? - Computing Acronyms And Abbreviations
-
NIP - Network Independent Protocol
-
Inside NIP Hype | Network Computing