What Is Registration Authority (RA)? - TechTarget
Maybe your like
- Home
- Identity and access management
- Rahul Awati
- Andrew Froehlich, West Gate Networks
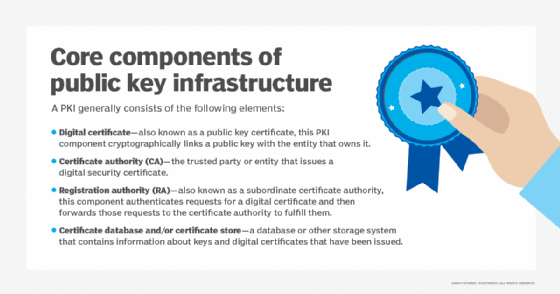
A registration authority (RA) is an entity that is authorized to verify user requests for a digital certificate and also to tell a certificate authority (CA) to issue that certificate to the user. RAs are an important part of a public key infrastructure (PKI), a networked system that enables companies and users to exchange information and money safely and securely. The digital certificate issued by the CA -- after verification by the RA -- contains a public key that the user can apply to encrypt and decrypt messages and digital signatures.
Understanding the role of a registration authority
The RA cannot create or issue a certificate; this is the sole responsibility of the CA. This segregation of responsibility is important for security purposes. In the PKI system, RAs typically process the following tasks:
- Receive user or device certificate requests.
- Validate users or devices.
- Authenticate users or devices.
- Revoke credentials if the certificate is no longer valid.
RAs implement proven business logic and methods to verify users' certificate requests. During verification, they can check the applicant's identity and other information that will be included on the digital certificate.
Once the verification is completed, the RA forwards the certificate request to the CA. The RA provides a signed statement confirming that it completed the user's authentication and has confirmed the user's identity. The CA then validates the RA's message and completes the digital certificate request process. The issued certificate validates the certificate holder's identity (and that it has been certified) and includes the key that will allow the holder to encrypt and decrypt messages in digital communications.
How do RAs work?
When a user or device requests a digital certificate to prove its authenticity in digital communications, a process must be in place to verify the requester's identity. Thus, the requester's first step in this process is to gain permission through a registration authority service.
The requester's certificate request is sent to the PKI's RA to verify that the requester has the right to request the certificate. The RA verifies the user's (or device's) identity and processes authentication credentials. The RA's involvement in the authentication process relieves this burden from the CA, which can then focus on issuing the certificate.
If everything checks out, the RA forwards the certificate request to the CA to process. The CA then issues the digital certificate directly to the requesting user or device. If the RA denies the request, the requester is not permitted to continue the certificate request process. The RA functions as a proxy between the user and the CA.
A successful digital certificate request process happens in the following order:
- A user attempting to access a certificate-backed website requests the certificate from the CA. This request is sent to the web server.
- The web server forwards the certificate request to the RA.
- The RA decides if the user is allowed to receive a certificate.
- If the RA grants the request, it is passed to the CA, which generates the digital certificate.
- The CA sends the digital certificate directly to the user to complete the certificate issuance process.
What is a local registration authority (LRA)?
A local RA is typically responsible for a local community, such as an organization, a branch, a department or a region. By operating in a smaller, more localized context, LRAs facilitate more nuanced and tailored management of standards compliance. Additionally, the limited focus area of LRAs allows them to be more responsive to the unique needs of the stakeholders within that specific community.
By offloading certain responsibilities to one or more LRAs -- including the preliminary assessment of applications for digital identifiers -- central RAs can more easily distribute and manage those identifiers, and maintain the rigor of the identifier distribution/management process. This is important to ensure that certificate requesting entities properly comply with relevant standards and establish a trusted digital environment. The initial vetting of applications by the LRA also speeds up the final processing of the certificate request by the centralized RA.
LRAs also provide support and guidance to further help entities comply with security standards. Since the LRA understands the local context and challenges, they are better able to troubleshoot and resolve issues, as well as help entities navigate the complexities of compliance. In doing so, LRAs help to not only ensure standards compliance, but also to strengthen the security of the overall digital ecosystem.
What is the difference between certificate authority and registration authority?
A registration authority can be thought of as a gatekeeper to a certificate authority. In order to be issued a certificate, the requesting user or device must first register with the RA and fulfill the necessary requirements, including identity and authentication checks. This comes in the form of a certificate signing request. The checks performed by the RA are critical to verify the requester's identity and, therefore, prevent fraud.
Only after the RA successfully validates the requester's identity can the certificate request be forwarded to the CA. Once the CA receives this request, it is its responsibility to issue the digital certificate to the requesting user or device. This electronic document can be validated against the CA's public key to ensure its validity for use in digital communications and transactions.
The connection between CA, RA and DRA
A registration authority works as a trusted agent or intermediary for the CA to collect the information necessary to verify the identity and other details of a certificate requesting user. The RA's role is to authenticate the identity of a certificate requesting entity, and the CA's role is to accept the RA's request, process it, and issue the certificate to the requester. Both the CA and RA are trusted entities that are crucial to the functioning and security of the digital world.
A delegate registration authority (DRA) acts on behalf of an RA -- although they can also act on behalf of a CA -- to authenticate a requester's identity. They might also be called upon by a CA or RA to revoke an existing certificate.
Managing digital certificates can be tedious and challenging. Learn how certificate automation can help simplify this task.
Continue Reading About What is a registration authority (RA)?
- Prepare for quantum to fundamentally change PKI effectiveness
- Types of PKI certificates and their use cases
- The benefits and challenges of managed PKIs
- Use these user authentication types to secure networks
- Roll out IoT device certificates to boost network security
Related Terms
What is a message authentication code (MAC)? How it works and best practices A message authentication code (MAC) is a cryptographic checksum applied to a message to guarantee its integrity and authenticity. See complete definition What is biometric authentication? Biometric authentication is a security process that relies on the unique biological characteristics of individuals to verify ... See complete definition What is identity and access management? Guide to IAM No longer just a good idea, IAM is a crucial piece of the cybersecurity puzzle. It's how an organization regulates access to ... See complete definitionDig Deeper on Identity and access management
-
![]()
What is a certificate authority (CA)?
 By: Rahul Awati
By: Rahul Awati -
![]()
What is a certificate revocation list (CRL) and how is it used?
 By: Rahul Awati
By: Rahul Awati -
![]()
What is a public key certificate?
 By: Rahul Awati
By: Rahul Awati -
![]()
What is PKI (public key infrastructure)?
 By: Rahul Awati
By: Rahul Awati
- How to Level Up the Revenue Cycle Management Game Plan –Greenway Health
- Three Innovative AI Use Cases for Natural Language Processing –Dell Technologies
- See More
- Buyer’s Guide for Machine Identity Management –Venafi & Intel
- Cryptography for Dummies –Entrust, Inc.
- Networking
- CIO
- Enterprise Desktop
- Cloud Computing
- Computer Weekly
- Macrocell vs. small cell vs. femtocell: A 5G introduction
Macrocells, small cells and femtocells each play distinct roles in 5G, balancing coverage, speed, cost and indoor connectivity ...
- What are the features and benefits of 5G technology?
Increased cellular speed, bandwidth and capacity at lower latencies have made wireless VR and AR practical for business use, ...
- Wi-Fi 6 vs. 5G: What's the difference?
Wi-Fi 6 and 5G both boost speed and performance, but differ in cost, coverage and use cases. Together, they provide flexible ...
- From CIO to CEO: Unlocking the entire C-suite
CIOs can evolve from technology leaders to enterprise strategists, taking on higher C-suite roles by building profit and loss ...
- How AI Is reshaping IT leadership and the modern CIO
Internal IT succession planning develops CIO-ready leaders, reduces disruption and strengthens organizational resilience through ...
- Predictable IT spending in an unpredictable economy
As AI and volatility push costs higher, CIOs must adopt flexible budgeting -- rolling forecasts, FinOps and real-time metrics -- ...
- How to use Windows Check Disk to maintain disk health
Using built-in Windows tools such as Check Disk and SMART helps organizations reduce risks associated with disk errors, extend ...
- How IT admins can check BIOS or UEFI versions in Windows 11
Firmware, such as BIOS or UEFI, plays a crucial role in how securely a Windows device starts and operates. Organizations need to ...
- Microsoft opens Copilot agent building to office rank and file
The battle for desktop agent mindshare heats up. Microsoft is the latest to arm everyday office workers with tools to make their ...
- Nutanix sovereign cloud hits Broadcom with multi-cloud hook
Nutanix expands its differentiation from Broadcom with a distributed sovereign cloud approach that supports both self-managed and...
- Plan for repatriation on day one with a hybrid cloud strategy
In the next 2 years, 87% of orgs plan to repatriate workloads off public cloud. Discover how an exit strategy, paired with hybrid...
- AWS CloudOps hones multi-cloud support for AI, resilience
Network, observability and Kubernetes management news at re:Invent aligned around themes of multi-cloud scale and resilience amid...
- Top 10 India stories of 2025
From infrastructure expansion and sovereign AI innovation to regulatory maturity, Computer Weekly recaps the key developments ...
- Top 10 networking stories of 2025
As enterprises become more extended, dealing with network complexity has become almost as important as network performance. The ...
- Top 10 cyber crime stories of 2025
In many regards, 2025 proved to be a relatively normal year for the cyber security world as threat actors and security pros ...
Tag » What Does Ra Stand For
-
Rheumatoid Arthritis (RA) | Arthritis | CDC
-
RA - What Does RA Stand For? The Free Dictionary
-
What Does RA Stand For?
-
Ra - All Meanings - Abbreviations
-
RA Meanings | What Does RA Stand For? - All Acronyms
-
Ra Definition & Meaning - Merriam-Webster
-
Rheumatoid Arthritis: MedlinePlus Medical Encyclopedia
-
What Does RA Mean? - Business - Definition And Meaning Of RA
-
ED, EA, RD, RA - What Do These Stand For In College? - Bound4College
-
What Does RA Stand For In Texting? 20 Meanings Of RA
-
What Does RA Stand For In Government And Military? 73 Meanings ...
-
Ra - Urban Dictionary
-
What Does RA Mean? - RA Definitions - Abbreviation Finder
-
RA - Definition By AcronymAttic



