All That Port 8000 Traffic This Week! Yeah, That's Satori Looking For ...
Có thể bạn quan tâm

The mystery of the recent surge in port 8000 scan activity has been solved today by security researches from Qihoo 360 Netlab, who tracked this week's mystery traffic to an old foe —the Satori IoT botnet.
According to researchers, the publication of proof-of-concept (PoC) code on June 8 for a popular web server software package drew the attention of the Satori crew, who integrated that particular exploit into their botnet's attack routine.
XionMai PoC results in a spike of port 8000 scans
The PoC code was for a buffer overflow vulnerability (CVE-2018-10088) in XionMai uc-httpd 1.0.0, a lightweight web server package often found embedded inside the firmware of routers and IoT equipment sold by some Chinese vendors.

The exploit allows an attacker to send a malformed package via ports 80 or 8000 and execute code on the device, effectively taking it over.
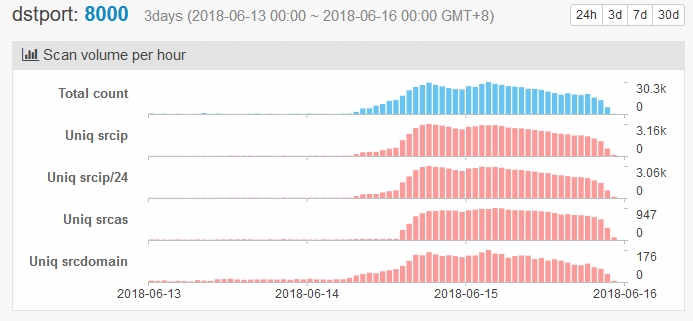
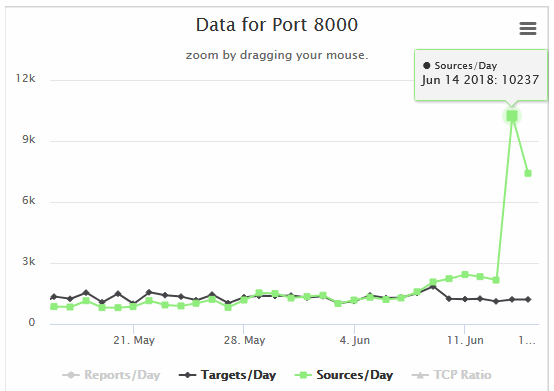
Scans for devices that had port 8000 exposed via their WAN interface started a day after the PoC's publication but picked up yesterday, June 14. The sudden surge in port 8000 activity turned the heads of multiple security experts specialized in botnet tracking, as it came out of nowhere and at an incredible scale.
What's up with all the 8000/tcp traffic?
— Bad Packets Report (@bad_packets) June 14, 2018
port 8000 scan is also jumping up now...stay tuned for more update https://t.co/GiJhJRKMkA https://t.co/CI3afTOQha
— 360 Netlab (@360Netlab) June 15, 2018
Here's a link to the pcap file (traffic to & from port 8000). Definitely captured some traffic but nothing jumped out to me as malicious. Unusual, but not malicious. Always possible that I missed something, though.https://t.co/Ktooo5tryc
— ExecuteMalware (@executemalware) June 14, 2018
|
|
|
Satori incorporates D-Link exploit
According to honeypot data from Qihoo 360 Netlab and SANS ISC, port 8000 scans started to die down today. Unfortunately, it wasn't because Satori was failing to infect devices, but because the botnet's authors added support for a second exploit.
This second exploit is also based on PoC code published online, but last month. The PoC is for a vulnerability affecting D-Link DSL-2750B routers, which can be exploited via ports 80 and 8080.
Naturally, scan activity targeting these two ports also grew similarly to the one seen on port 8000, and the Satori crew is trying to corral as many routers as it can before other botnets join the fold.
After previously targeting GPON routers, and with the addition of these two new exploits, Satori continues to grow with every day. The botnet has already survived a takedown attempt last December, and its authors seem intent on continuing on their current path.
While some IoT botnets try to avoid the limelight by just re-routing traffic for other crooks, Satori is more of an in-your-face botnet, used to hijack cryptocurrency miners and steal funds, or launch disruptive DDoS attacks. Just this week, Qihoo 360 Netlab says Satori carried out two such attacks [1, 2].
Indicators of compromise for the recent Satori versions are available in Netlab's recent report.

The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
Get the guideRelated Articles:
New Linux botnet SSHStalker uses old-school IRC for C2 comms
DKnife Linux toolkit hijacks router traffic to spy, deliver malware
Aisuru botnet sets new record with 31.4 Tbps DDoS attack
Cloudflare misconfiguration behind recent BGP route leak
New GoBruteforcer attack wave targets crypto, blockchain projects
Từ khóa » Http-alt 8000
-
Port 8000 (tcp/udp) :: SpeedGuide
-
RFC 7838 - HTTP Alternative Services
-
Port 8000 Vs Port 8080 - Stack Overflow
-
TCP Port 8000 Activity To The Internet | SIEM Guide [7.8] - Elastic
-
ALT-8000 FMCW/Pulse Radio Altimeter Flight Line Test Set
-
HTTP Alternate Services - IETF Tools
-
RFC 7838 - HTTP Alternative Services - IETF Tools
-
How Do I Get My Devices Connected On Port 8000 For ... - Ask Ubuntu
-
HackTheBox – Luke | InfoSec @ Rm-it
-
List Of TCP And UDP Port Numbers - Wikipedia
-
Enumerate Applications On Webserver - OWASP Foundation
-
AEROFLEX ALT-8000 OPERATION MANUAL Pdf Download