What Is PHI (Protected/Personal Health Information)? - TechTarget
- Home
- Heathcare policy and regulation
Data protection is the process of safeguarding data and restoring important information in the event that the data is corrupted, compromised or lost due to cyberattacks, shutdowns, intentional harm or human error. It embraces the technologies, practices, processes and workflows that ensure rightful access to data, so the data is available when it's needed. Use this guide to explore more about data protection, including key principles, best practices, technologies and trends.
By- Cameron Hashemi-Pour, Former Site Editor
- Ben Lutkevich, Site Editor
- Scott Wallask
Protected health information (PHI), also referred to as personal health information, is the demographic information, medical histories, test and laboratory results, physical and mental health conditions, insurance information and other data that a healthcare professional collects to identify an individual and determine appropriate care.
The Health Insurance Portability and Accountability Act (HIPAA) of 1996 is the primary law that oversees the use of, access to and disclosure of PHI in the United States. HIPAA defines PHI as data that relates to the past, present or future physical or mental health of an individual; the provision of healthcare to an individual; or the payment for the provision of care to an individual. HIPAA regulates how this data is collected, created, received, transmitted, maintained and stored by any HIPAA-covered organization.
Healthcare deals with sensitive details about a patient, including birthdate, medical conditions and health insurance claims. Whether in a paper-based record or an electronic health record (EHR) system, PHI explains a patient's medical history, including ailments, treatments and outcomes.
What is considered personal health information?
HIPAA lists 18 different information identifiers that, when paired with health information, become PHI. Some of these identifiers on their own allow an individual to be identified, contacted or located. Others must be combined with other information to identify a person.
This article is part of
What is data protection and why is it important?
- Which also includes:
- AI and GDPR: How is AI being regulated?
- How to conduct a data privacy audit, step by step
- Top data protection software vendors for business in 2026
The 18 identifiers are the following:
- Name.
- Geographic location or address more local than state.
- Dates (except years) related to an individual, such as birth, procedure and admission dates.
- Phone number.
- Fax number.
- Email address.
- Social Security number.
- Medical record number.
- Health plan beneficiary number.
- Account number.
- Certificate or license number.
- Vehicle identifiers, such as serial and license plate numbers.
- Device identifiers and serial numbers.
- Web URL.
- Internet Protocol address.
- Biometric identifiers, such as a fingerprint or voice print.
- Full-face photographs and other photos of identifying characteristics.
- Any other unique identifying characteristic.
How is PHI used?
From the first moments after birth, a baby will likely have PHI entered into an EHR, including weight, length, body temperature and any complications during delivery. Tracking this type of medical information during a patient's life offers clinicians the context they need to understand a person's health and make treatment decisions.
Clinical and research scientists use anonymized PHI to study health and healthcare trends. Researchers use PHI that's stripped of identifying features and added anonymously to large databases of patient information for population health management studies. Such anonymized PHI is also used to create value-based care programs that reward healthcare providers for providing quality care.
Hackers and cybercriminals take a keen interest in PHI. It's a treasure trove of personal consumer information that they can sell. Criminals also hold PHI hostage through ransomware attacks. They attempt to force a healthcare provider or other organization to provide a payoff in exchange for their PHI, which the threat actor had made inaccessible.
HIPAA and the Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009 limit the types of PHI healthcare providers, health insurance companies and the companies they work with can collect from individuals. Those regulations also limit what those organizations can do with the data in terms of sharing it with other organizations or using it in marketing. In addition, organizations must provide a patient's PHI to them if requested, preferably in an electronic PHI (ePHI) format.
How is ePHI collected and stored?
Electronic PHI is a subset of PHI where health information is collected, transmitted and stored electronically. The list of devices involved includes the following:
- Databases and other forms of storage.
- Internal hard drives, such as those in personal computers.
- External hard drives.
- Magnetic tapes.
- Smartphones and other mobile devices, such as wearable monitors and medical devices.
- Removable storage devices, such as USB drives.
Electronic PHI must be handled in accordance with HIPAA and other laws and regulations. Organizations typically have policies covering that, including how the data is collected, transmitted, altered and destroyed. They must designate clear roles and responsibilities for data handling, and train employees to follow policies and comply with all regulations.
Security measures such as encryption and access controls are crucial for securing ePHI, both at rest and in transit. For example, employees' access to ePHI data should be limited to data they need to do their job.
PHI loss or theft is still possible even with adequate security measures and policies in place. Organizations must consider creating backup copies of data and using cloud storage platforms to keep them safe. Physical, on-premises devices normally used to store ePHI are more susceptible to outages and attacks; cloud storage is a good strategy for securing ePHI copies.
What are covered entities under HIPAA?
Any organization or individual that handles PHI regularly is categorized under HIPAA as a covered entity and must follow the regulation's security and privacy rules. Providers, insurers and healthcare clearinghouses are considered covered entities.
A third party that handles PHI on behalf of a covered entity is considered a business associate under HIPAA and subject to HIPAA rules. For instance, a health information exchange (HIE) is a service that lets healthcare professionals access and share PHI. Because it is involved in transmitting the PHI on behalf of the covered entity -- the healthcare provider -- the HIE is a business associate and must comply with HIPAA's regulations.
HIPAA privacy rule
The main regulation that governs the secure handling of PHI is the HIPAA Privacy Rule. It governs how hospitals, ambulatory care centers, long-term care facilities and other healthcare providers use and share PHI. It provides federal protections for PHI that covered entities hold and gives patients certain rights with respect to that information. The HIPAA Privacy Rule specifies when the disclosure of PHI is permitted, such as to ensure the health and safety of the patient and to communicate with individuals the patient says can receive the information.
Organizations can't sell PHI unless in one of the following circumstances:
- For a public health purpose that HIPAA allows.
- For research, but only for reimbursement of costs.
- For treatment and present or future payment as allowed by HIPAA.
- As part of the merger or acquisition of a HIPAA-covered entity.
HIPAA also gives individuals the right to make written requests to amend PHI that a covered entity maintains.
Partners of healthcare providers and insurers that sign HIPAA business associate agreements are legally bound to handle patient data according to the HIPAA Privacy and Security Rules. Business associates, as well as covered entities, are subject to HIPAA audits, conducted by the U.S. Department of Health and Human Services' (HHS) Office for Civil Rights. HIPAA violations are costly and can damage a business's reputation.
Protected health information was originally intended to apply to paper records. Since the passage of the HITECH Act and the replacement of paper health records with EHRs, HIPAA has governed electronically stored patient data. HIPAA rules regulate paper and electronic data sets equally, but there are differences between the two formats.
First, covered entities must respond to patients' requests for access to their data within 30 days, a timeframe created to accommodate the transmission of paper records. However, the HIPAA rules state that if the provider is using health IT, the patient should be able to get the records faster.
The PHI disposal methods also vary between electronic and paper records. Paper files are shredded or otherwise made unreadable and unable to be reconstructed. Electronic PHI must be cleared or purged from the system in which it was held.
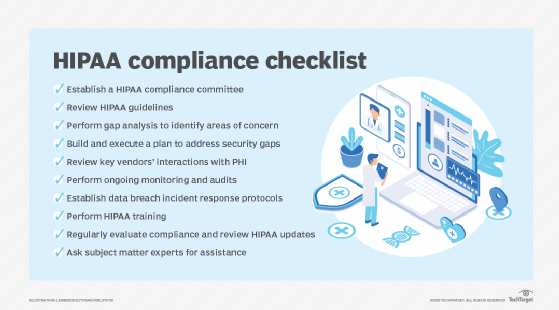
HIPAA compliance and security
The HIPAA Security Rule encompasses measures that restrict unauthorized access to PHI. Covered entities must defend against threats to PHI that can be reasonably anticipated. It also requires technical, administrative and physical safeguards to protect PHI.
What follows are examples of these three safeguards:
- Technical safeguards cover the use of firewalls, encryption, access controls and other technology.
- Physical safeguards include locking up physical records, keycards and other access controls on electronic devices containing PHI, making screens unreadable to anyone except the user, and other measures.
- Administrative safeguards include policies that limit PHI access to certain people, safety awareness training and other people-based approaches to security.
Covered entities must evaluate IT capabilities and the likelihood of a PHI security risk. HIPAA rules don't specify the types of technology needed, but covered organizations must take action to keep hackers and malware from gaining access to patient data.
Other regulations affecting PHI, include the European Union's General Data Protection Regulation (GDPR). It applies to a broader set of health data, including genetics. Healthcare organizations that treat EU patients must adhere to the GDPR regulations about patient consent to process PHI.
Also, in 2018, the U.S. federal government announced the MyHealthEData program, in which the government promotes the idea that patients should control their PHI and that patients can transfer data from one doctor to another. The underlying point of MyHealthEData is to encourage healthcare organizations to pursue interoperability of health data as a way of allowing patients more access to their records.
In recent years, the HHS proposed changes to HIPAA, but the Security Rule has largely remained intact. However, more recent HHS proposals include the department publishing voluntary cybersecurity performance goals in January 2024 to encourage healthcare providers to strengthen their data security and disaster recovery measures. Additionally, the department published an update to HIPAA's Privacy Rule to encompass reproductive health data as well in June 2024, having done so through its Office of Civil Rights.
What is the difference between PII, PHI and IIHI?
It's important to distinguish between personally identifiable information (PII), PHI and a third type: individually identifiable health information (IIHI):
Personally identifiable information
PII is any data used to identify someone. It could be nonsensitive data that can be transmitted and stored publicly without resulting in harm to the individual. Or it could be sensitive data that, if disclosed, might harm the individual. PII also encompasses more than just health information. It includes information such as tax information, credit card numbers and Social Security numbers used in a context unrelated to healthcare operations and services. Protecting PII is only mandated in certain instances, such as when it's being used in a healthcare context or combined with healthcare information.
Protected health information
PHI is information used in a medical context. Organizations handling PHI must always comply with HIPAA rules.
Individually identifiable health information
IIHI is health information that can identify a person. It's essentially PII in a health context. Not all IIHI is protected under HIPAA. IIHI that a HIPAA-covered entity hasn't handled, transmitted, maintained or stored is IIHI that doesn't qualify as PHI. For example, if a patient takes daily blood pressure readings on a paper form that includes their name, address and phone number but they don't send it to their doctor, that would be IIHI that's not PHI. Although it might be sensitive, because it hasn't been transmitted, it isn't protected.
In other words, IIHI becomes PHI in the following circumstances:
- IIHI transmitted by electronic media, such as email.
- IIHI maintained in electronic media, such as on a server.
- IIHI transmitted or maintained in a physical location used by a HIPAA- or GDPR-covered provider.
PHI and healthcare apps
EHRs are a common area where PHI and IT intersect, as are health information exchanges. Vendors create HIEs to enable healthcare providers to access and transmit PHI properly. These third-party vendors are responsible for developing applications that are HIPAA-compliant.
Developing a healthcare app, particularly mobile health applications, such as heart rate or blood sugar monitors, that use PHI and are HIPAA compliant is expensive and time-consuming. Apps for tracking personal health metrics that don't transmit PHI data anywhere aren't subject to HIPAA rules. However, texting, image sharing, video conferencing and any other app where patients discuss or share PHI with healthcare providers must be HIPAA-compliant and have the required security measures to protect data.
Ensuring that all privacy and security safeguards are in place is challenging. Some developers work with cloud providers that are certified to host or maintain the parts of the service's stack that need to be HIPAA compliant.
Wearable technology that collects biometric data poses unique challenges when it comes to regulatory compliance and securing PHI. These devices collect a diverse set of information, including medical, exercise and biological data such as heart rates and sleep patterns, and it's not always clear what data must be protected.
Often, patients use wearables to monitor their health metrics without sharing the information with their healthcare provider. In those cases, HIPAA compliance doesn't apply. If an organization developing the wearable plans to retain user data for research or other purposes, it might need to comply with HIPAA and get informed consent from users.
Read more about PHI and wearable devices
How connected health tech bolsters chronic care, behavioral health
Wearables linked to pathologic heart disease symptom monitoring
Why Sutter Health is using a wearable device for critical care
How wearables can enhance cardiac care, boost patient engagement
Many healthcare-related apps don't have to comply with HIPAA. Scenarios where an application must comply with HIPAA include the following:
- If a covered entity develops a healthcare app that collects or interacts with PHI, the information must be protected in compliance with HIPAA.
- If a physician recommends that a patient use a healthcare app, the information collected isn't covered, because the app wasn't developed for the physician to use. However, if the data from the app is added to the patient's EHR, it is covered.
- If a third-party developer makes an app for physicians to use that collects PHI or interacts with it, the third party is a business associate handling PHI on behalf of the physician, and HIPAA applies to the business associate.
Common misconceptions about PHI
Another area of misinterpretation is that PHI privacy and security don't always move in tandem. It's possible to have security restrictions in place that don't fully protect privacy under HIPAA mandates. For example, if a cloud vendor hosts encrypted PHI for an ambulatory clinic, privacy could still be an issue if the cloud vendor isn't part of a business associate agreement. Under HIPAA, the cloud vendor is responsible for the integrity of the hosted PHI, as well as its security.
Also, PHI shouldn't be confused with a personal health record (PHR), which a patient maintains and updates using services such as the Apple Health application.
With a PHR, patients oversee the security of the data themselves, akin to consumers guarding their credit card numbers and other personal information. However, the lines between PHR and PHI will blur in the future as more digital medical records are accessed and shared by patients.
Managing and analyzing patient data on a large scale is challenging. Learn how data analytics tools are used for patient data.
Continue Reading About What is PHI (protected or personal health information)?
- Top ways artificial intelligence will impact healthcare
- How to properly dispose of electronic PHI under HIPAA
- How do population health, public health and community health differ?
- What is the Health Breach Notification Rule, who does it apply to?
- Change healthcare cyberattack exposes security concerns
Related Terms
What is Centers for Medicare & Medicaid Services (CMS)? The Centers for Medicare & Medicaid Services (CMS) is part of the U.S. Department of Health and Human Services. See complete definition What is HIPAA (Health Insurance Portability and Accountability Act)? HIPAA (Health Insurance Portability and Accountability Act) is United States legislation that provides national standards to ... See complete definition What is HL7 (Health Level Seven International)? HL7 (Health Level Seven International) is an accredited, not-for-profit organization that develops frameworks and standards used ... See complete definitionDig Deeper on Heathcare policy and regulation
-
![]()
What is HIPAA (Health Insurance Portability and Accountability Act)?
 By: Katie Terrell Hanna
By: Katie Terrell Hanna -
![]()
What is PHI breach (protected health information breach)?
 By: Rahul Awati
By: Rahul Awati -
![]()
OCR updates HIPAA FAQs following health tech initiative launch
 By: Jill Hughes
By: Jill Hughes -
![]()
How updated third-party tech guidance affects compliance efforts
 By: Jill Hughes
By: Jill Hughes
- Strong warning issued to hospitals by HHS about EHR security –Commvault + Microsoft
- AI & Healthcare: Truth Behind the Buzz and a Path Forward –Greenway Health
- See More
- Healthcare Security & Compliance –TechTarget
- Rev Cycle Management
- Patient Engagement
- Healthtech Analytics
- Healthtech Security
- Virtual Healthcare
- CMS announces new ACO model as REACH ends
CMS unveiled the Long-Term Enhanced ACO Design, or LEAD, Model, that will run for ten years following the end of the popular ACO ...
- C-suite expects value-based care participation to heat up
Hospital and health system executives are investing more in value-based care models, including ACOs and bundled payments, ...
- More primary care practices ditch insurance for direct care
A study reveals an increasing number of practices and clinicians transitioning to concierge and direct primary care models in a ...
- 1 in 4 patients delay care, cite healthcare affordability issues
A new study takes a longitudinal look at healthcare affordability problems, finding the issue is more pervasive than previously ...
- What patients want to know about AI ambient scribing
UC Davis Health found patients want to know when AI ambient scribing is being used, that the tool is secure and that their ...
- How docs can manage patients consulting AI medical advice
Researchers recommend providers lead with empathy when patients bring in AI-generated medical advice and then move into shared ...
- HHS seeks info to guide AI regulation, reimbursement
HHS is seeking feedback from stakeholders on regulations, reimbursement models and research initiatives that will accelerate AI ...
- New framework aims to drive ethical AI use in mental health
Spring Health has introduced an ethical AI framework for mental health amid an FDA committee review of generative AI digital ...
- HHS outlines strategy to expand AI adoption
Although the strategy is internally focused, HHS said it will collaborate with the private sector and identify “priority” ...
- 10 largest healthcare data breaches reported to OCR in 2025
More than 20 million individuals were affected by the 10 largest healthcare data breaches reported to OCR in 2025.
- Governance gaps threaten progress as healthcare AI adoption grows
Health systems are relying on AI faster than their governance structures can evolve, expanding the potential for data privacy ...
- OCR settles 54th HIPAA right of access case
Occupational health services provider Concentra will pay OCR $112,500 to resolve alleged HIPAA right of access failures.
- Physicians' telehealth use varies across specialties, practice type
New AMA data reveals that telehealth utilization among physicians has only dropped slightly since 2022; however, factors such as ...
- Exploring Nemours' pediatric at-home care program
Nemours Children's Health launched an at-home care program leveraging telehealth and RPM that aims to enhance patient recovery ...
- Most nurses say that virtual nursing does not reduce workloads
Not only did most nurses report that virtual nursing did not alleviate their workloads, but about 10% also believe that it ...
Từ khóa » Phi Vs Non Phi
-
What Is Considered Protected Health Information Under HIPAA?
-
What Is PHI And What Is Not PHI? - Mobisoft Infotech
-
Understanding What Is And Is Not PHI - HIPAA Exams
-
What Is Considered PHI Under HIPAA? 2022 Update - HIPAA Journal
-
Protected Health Information (PHI) - TrueVault
-
The ABCs Of PHI—Plus: Protected Health Information Decision Tree
-
[PDF] What Is And Is Not Protected Health Information (PHI) In Research ...
-
HIPAA PHI: List Of 18 Identifiers And Definition Of PHI - UC Berkeley
-
PHI Is Protected Health Information: Healthcare's Most Valuable Asset
-
Key Differences Between PHI And PII, How They Impact HIPAA ...
-
HIPAA Protected Health Information | Understanding PHI
-
PHI Vs PII - The Difference Between PII And PHI - ForeSee Medical
-
What Is PHI Under HIPAA? Requirements For Compliance



