What Is Soc 2 (Service Organization Control 2)? - TechTarget
Có thể bạn quan tâm
What are the Trust Services Criteria?
At the heart of the SOC 2 standard is the Trust Services Criteria (TSC), an extensive set of criteria that expands on each Trust Services Principle. According to the AICPA: "The TSC are control criteria for use in attestation or consulting engagements to evaluate and report on controls over information and systems (a) across an entire entity; (b) at a subsidiary, division or operating unit level; (c) within a function relevant to the entity's operational, reporting or compliance objectives; or (d) for a particular type of information used by the entity."
AICPA classifies the TSC into five broad categories, which provide a structure for understanding the general nature of the underlying criteria:
- Security. Systems are protected against unauthorized access or disclosure of sensitive information, as well as against system damages that could compromise data availability, integrity, confidentiality or privacy.
- Availability. The protected systems and information meet the availability and use requirements defined by the organization's objectives.
- Processing integrity. Processing operations are complete, accurate, timely and secure, as required by the organization's objectives.
- Confidentiality. Systems and operations meet the confidentiality requirements defined by the organization's objectives.
- Privacy. All personally identifiable information meets the collection, usage, retention, disclosure and disposal requirements defined by the organization's objectives.
The five categories provide a way for organizations to understand the scope of SOC 2 auditing and reporting and to get a sense of how auditors approach their evaluations. However, the actual organization of the TSC in the SOC 2 standard is far more complex.
The bulk of the standard is made up of the TSC, which are organized into 13 trust categories: five core categories, four supplemental categories and four specialty categories. Each category includes multiple Trust Services Principles, and each principle includes a set of related criteria.
For example, the first trust category is Control Environment (Trust ID CC1). The Common Criteria 1 (CC1) trust category contains five principles. The first principle, CC1.1, states that the "entity demonstrates a commitment to integrity and ethical values."
The CC1.1 principle includes five criteria, which are referred to as the points of focus. The first criterion is concerned with the overall tone: "The board of directors and management, at all levels, demonstrate through their directives, actions and behavior the importance of integrity and ethical values to support the functioning of the system of internal control."
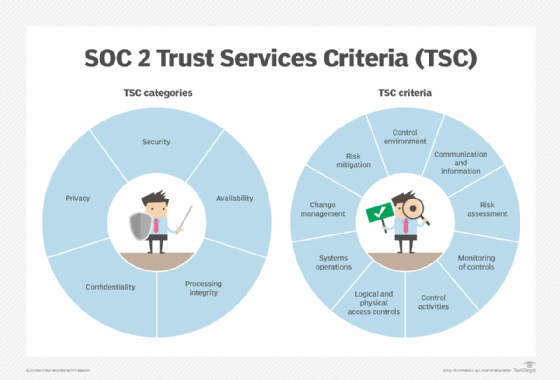
The core and supplemental trust categories are numbered consecutively -- CC1 through CC9 -- and often grouped together:
- Control Environment (CC1). The criteria focus on the organization's commitment and efforts to carry out its objectives and support the functioning of internal controls.
- Communication and Information (CC2). The criteria are concerned with the organization's ability to gather, disseminate and communicate information relevant to meeting its objectives.
- Risk Assessment (CC3). The criteria address the organization's ability to identity, assess and manage the risks associated with meeting its objectives.
- Monitoring Activities (CC4). The criteria are concerned with the organization's ability to select, implement and manage internal controls and respond to control deficiencies in a timely manner.
- Control Activities (CC5). The criteria focus on how the organization selects, develops and deploys control activities and on its ability to put policies into action.
- Logical and Physical Access Controls (CC6). The criteria address the organization's ability to implement software and infrastructure controls over protected assets and to manage user access to protected data.
- System Operations (CC7). The criteria focus on the organization's ability to monitor and detect vulnerabilities, configuration changes and anomalous behavior and to respond to security incidents.
- Change Management (CC8). The criteria are concerned with the organization's ability to design, document and implement changes in data, software, infrastructure and procedures.
- Risk Mitigation (CC9). The criteria address the organization's ability to identify, select and develop risk mitigation activities.
The core trust categories include the first five in the list, and the supplemental categories include the last four. In addition to these categories, the SOC 2 standard defines four supplemental trust categories that focus specifically on availability, processing integrity, confidentiality and privacy.
See also: SOC 1 and SOC 3.
Từ khóa » Sóc L
-
What Is SOC 2 | Guide To SOC 2 Compliance & Certification - Imperva
-
Sóc L'Spiderwoman From Judit Costa On Vimeo
-
SOC 2 Compliance On Warden - Horangi Cyber Security
-
SOC Compliance - Amazon Web Services (AWS)
-
SOC 2 Compliance: The Basics And A 4-Step Compliance Checklist
-
Service Organization Control (SOC) Reports - Alibaba Cloud's
-
SỞ Y TẾ HÀ NỘI - Quản Lý Người Nhiễm Covid-19
-
System And Organization Controls (SOC) 2 Type 2 - Microsoft Docs
-
Delinea Completes SOC 2 Type Ll Compliance Recertification
-
Gemini Completes SOC 1 Type 2 And SOC 2 Type 2 Examinations
-
SOC 2 Compliance At Paddle
-
What Is SOC 2 Compliance? Requirements, Definition - LogicGate
-
System And Organization Controls: SOC Suite Of Services - AICPA
-
SOC For Service Organizations - AICPA
-
Service Organization Control (SOC) 2 Report
-
How We're Building Assurance With SOC 2 Type 2 Compliance
-
SOC® 2 - 360 Advanced