What Is SQL Injection (SQLi) And How To Prevent Attacks - Acunetix
Có thể bạn quan tâm
What is SQL Injection (SQLi) and How to Prevent It
SQL Injection (SQLi) is a type of an injection attack that makes it possible to execute malicious SQL statements. These statements control a database server behind a web application. Attackers can use SQL Injection vulnerabilities to bypass application security measures. They can go around authentication and authorization of a web page or web application and retrieve the content of the entire SQL database. They can also use SQL Injection to add, modify, and delete records in the database.
An SQL Injection vulnerability may affect any website or web application that uses an SQL database such as MySQL, Oracle, SQL Server, or others. Criminals may use it to gain unauthorized access to your sensitive data: customer information, personal data, trade secrets, intellectual property, and more. SQL Injection attacks are one of the oldest, most prevalent, and most dangerous web application vulnerabilities. The OWASP organization (Open Web Application Security Project) lists injections in their OWASP Top 10 2017 document as the number one threat to web application security.
What are SQL Queries?
SQL is a query language that was designed to manage data stored in relational databases. You can use it to access, modify, and delete data. SQL queries are usually commands that request a specific set of results from the database using the SELECT statement, though other statements also exist to perform database operations, like UPDATE, DELETE, or DROP.
Applications incorporate user inputs into SQL queries to fetch the required data from their backend database. At its simplest, a SELECT statement to check user login credentials against the users table could be:
SELECT id FROM users WHERE username='user-input-here' AND password='user-input-here'This will return a user ID if the specified username and password combination exists and NULL (an empty result) otherwise. If the application code directly inserts raw user inputs into the query, it is most likely vulnerable to SQL injection.

How and Why Is an SQL Injection Attack Performed
To make an SQL Injection attack, an attacker must first find vulnerable user inputs within the web page or web application. A web page or web application that has an SQL Injection vulnerability uses such user input directly in an SQL query. The attacker can create input content. Such content is often called a malicious payload and is the key part of the attack. After the attacker sends this content, malicious SQL commands are executed in the database.
What is the Impact of a Successful SQL Injection Attack?
Many web applications and websites store all the data in SQL databases. In some cases, you can also use SQL commands to run operating system commands. Therefore, a successful SQL Injection attack can have very serious consequences.
- Attackers can use SQL Injections to find the credentials of other users in the database. They can then impersonate these users. The impersonated user may be a database administrator with all database privileges.
- SQL lets you select and output data from the database. An SQL Injection vulnerability could allow the attacker to gain complete access to all data in a database server.
- SQL also lets you alter data in a database and add new data. For example, in a financial application, an attacker could use SQL Injection to alter balances, void transactions, or transfer money to their account.
- You can use SQL to delete records from a database, even drop tables. Even if the administrator makes database backups, deletion of data could affect application availability until the database is restored. Also, backups may not cover the most recent data.
- In some database servers, you can access the operating system using the database server. This may be intentional or accidental. In such case, an attacker could use an SQL Injection as the initial vector and then attack the internal network behind a firewall.
Types of SQL Injections
There are several types of SQL Injection attacks: in-band SQLi (using database errors or UNION commands), blind SQLi, and out-of-band SQLi. You can read more about them in the following articles: Types of SQL Injection (SQLi), Blind SQL Injection: What is it.
In-band SQLi
“Regular” SQL injection is also called in-band SQLi because the attacker is able to receive results in the same way they performed the attack itself. A typical example would be to submit a web form with an SQLi payload and then see the returned database records on the same page.
Out-of-band SQLi
When an SQLi attack and its results use different channels, you have out-of-band (OOB) SQL injection. OOB attacks are used when the attacker can send a request but cannot see the response. Common OOB techniques include sending attack results to an attacker-controlled server and hiding them in DNS queries.
Inferential (Blind) SQLi
Blind SQL injection is an advanced technique for indirectly reconstructing small chunks of data. The main two types of inferential SQLi are timing-based and Boolean. Timing-based attacks rely on the database taking longer to respond to some queries than others, while Boolean attacks use a large number of yes/no questions to eventually home in on a specific value.
Second-order SQLi
Similar to stored XSS, second-order SQL injection payloads can also be stored in an external system and only executed when loaded by a user. While not as common as direct SQL injections, a single second-order attack could potentially affect a large number of users.
SQL Injection Examples
The first SQL Injection example is very simple. It shows, how an attacker can use an SQL Injection vulnerability to go around application security and authenticate as the administrator.
The following script is pseudocode executed on a web server. It is a simple example of authenticating with a username and a password. The example database has a table named users with the following columns: username and password.
# Define POST variables uname = request.POST['username'] passwd = request.POST['password'] # SQL query vulnerable to SQLi sql = “SELECT id FROM users WHERE username=’” + uname + “’ AND password=’” + passwd + “’” # Execute the SQL statement database.execute(sql)These input fields are vulnerable to SQL Injection. An attacker could use SQL commands in the input in a way that would alter the SQL statement executed by the database server. For example, they could use a trick involving a single quote and set the passwd field to:
password' OR 1=1As a result, the database server runs the following SQL query:
SELECT id FROM users WHERE username='username' AND password='password' OR 1=1'Because of the OR 1=1 statement, the WHERE clause returns the first id from the users table no matter what the username and password are. The first user id in a database is very often the administrator. In this way, the attacker not only bypasses authentication but also gains administrator privileges. They can also comment out the rest of the SQL statement to control the execution of the SQL query further:
-- MySQL, MSSQL, Oracle, PostgreSQL, SQLite ' OR '1'='1' -- ' OR '1'='1' /* -- MySQL ' OR '1'='1' # -- Access (using null characters) ' OR '1'='1' %00 ' OR '1'='1' %16Example of a Union-Based SQL Injection
One of the most common types of SQL Injection uses the UNION operator. It allows the attacker to combine the results of two or more SELECT statements into a single result. The technique is called union-based SQL Injection.
The following is an example of this technique. It uses the web page testphp.vulnweb.com, an intentionally vulnerable website hosted by Acunetix.
The following HTTP request is a normal request that a legitimate user would send:
GET http://testphp.vulnweb.com/artists.php?artist=1 HTTP/1.1 Host: testphp.vulnweb.com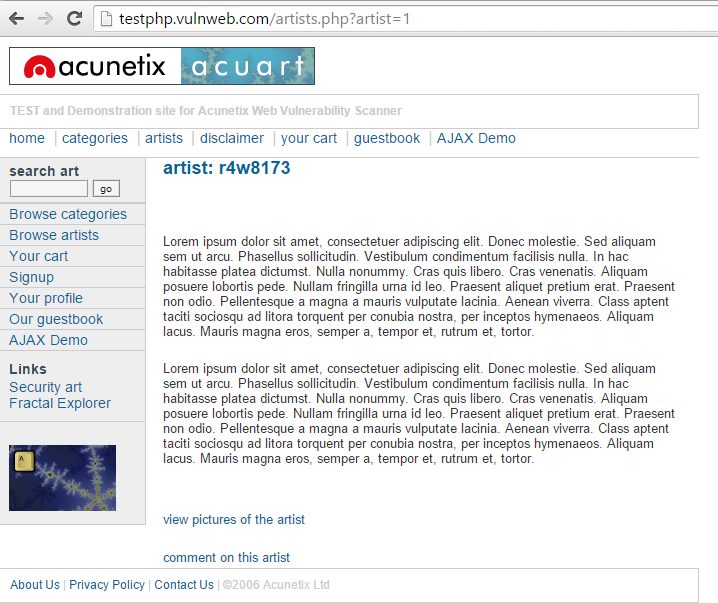
The artist parameter is vulnerable to SQL Injection. The following payload modifies the query to look for an inexistent record. It sets the value in the URL query string to -1. Of course, it could be any other value that does not exist in the database. However, a negative value is a good guess because an identifier in a database is rarely a negative number.
In SQL Injection, the UNION operator is commonly used to attach a malicious SQL query to the original query intended to be run by the web application. The result of the injected query will be joined with the result of the original query. This allows the attacker to obtain column values from other tables.
GET http://testphp.vulnweb.com/artists.php?artist=-1 UNION SELECT 1, 2, 3 HTTP/1.1 Host: testphp.vulnweb.com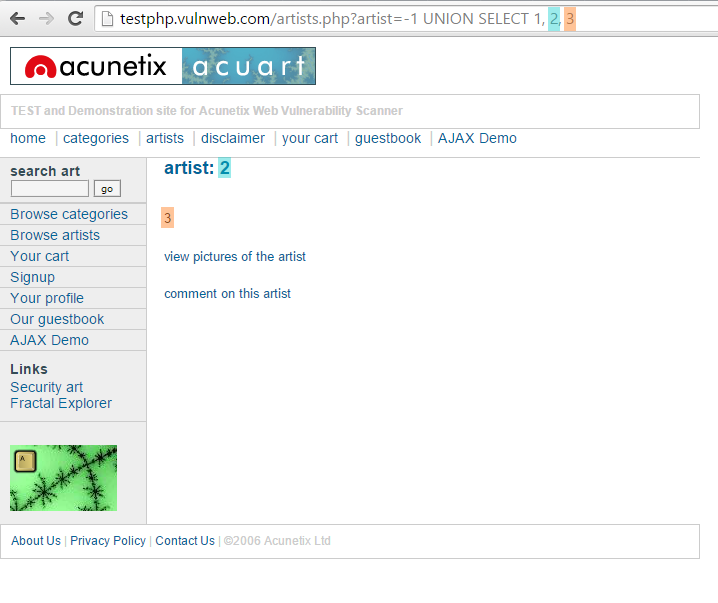
The following example shows how an SQL Injection payload could be used to obtain more meaningful data from this intentionally vulnerable site:
GET http://testphp.vulnweb.com/artists.php?artist=-1 UNION SELECT 1,pass,cc FROM users WHERE uname='test' HTTP/1.1 Host: testphp.vulnweb.com To follow step-by-step how an SQL Injection attack is performed and what serious consequences it may have, see: Exploiting SQL Injection: a Hands-on Example.
To follow step-by-step how an SQL Injection attack is performed and what serious consequences it may have, see: Exploiting SQL Injection: a Hands-on Example.
SQLi Prevention and Mitigation
The only sure way to prevent SQL Injection attacks is input validation and parametrized queries including prepared statements. The application code should never use the input directly. The developer must sanitize all input, not only web form inputs such as login forms. They must remove potential malicious code elements such as single quotes. It is also a good idea to turn off the visibility of database errors on your production sites. Database errors can be used with SQL Injection to gain information about your database.
If you discover an SQL Injection vulnerability, for example using an Acunetix scan, you may be unable to fix it immediately. For example, the vulnerability may be in open source code. In such cases, you can use a web application firewall to sanitize your input temporarily.
To learn how to prevent SQL Injection attacks in the PHP language, see: Preventing SQL Injection Vulnerabilities in PHP Applications and Fixing Them. To find out how to do it in many other different programming languages, refer to the Bobby Tables guide to preventing SQL Injection.
How to Prevent SQL Injections
Preventing SQL Injection vulnerabilities is not easy. Specific prevention techniques depend on the subtype of SQLi vulnerability, on the SQL database engine, and on the programming language. However, there are certain general strategic principles that you should follow to keep your web application safe.
 | Step 1: Train and maintain awarenessTo keep your web application safe, everyone involved in building the web application must be aware of the risks associated with SQL Injections. You should provide suitable security training to all your developers, QA staff, DevOps, and SysAdmins. You can start by referring them to this page. |
 | Step 2: Don’t trust any user inputTreat all user input as untrusted. Any user input that is used in an SQL query introduces a risk of an SQL Injection. Treat input from authenticated and/or internal users the same way that you treat public input. |
 | Step 3: Use whitelists, not blacklistsDon’t filter user input based on blacklists. A clever attacker will almost always find a way to circumvent your blacklist. If possible, verify and filter user input using strict whitelists only. |
 | Step 4: Adopt the latest technologiesOlder web development technologies don’t have SQLi protection. Use the latest version of the development environment and language and the latest technologies associated with that environment/language. For example, in PHP use PDO instead of MySQLi. |
 | Step 5: Employ verified mechanismsDon’t try to build SQLi protection from scratch. Most modern development technologies can offer you mechanisms to protect against SQLi. Use such mechanisms instead of trying to reinvent the wheel. For example, use parameterized queries or stored procedures. |
 | Step 6: Scan regularly (with Acunetix)SQL Injections may be introduced by your developers or through external libraries/modules/software. You should regularly scan your web applications using a web vulnerability scanner such as Acunetix. If you use Jenkins, you should install the Acunetix plugin to automatically scan every build. |
Further reading
Types of SQL Injection
A guide to preventing SQL Injection
SQL Injection Cheat Sheet
Frequently asked questions about SQL injection
What is SQL Injection?
SQL Injection is a web vulnerability caused by insecure coding. It allows an attacker to send commands to the database that the website or web application communicates with. This, in turn, lets the attacker get data from the database or even modify it.
See a step-by-step example of how SQL Injections happen.
How common are SQL Injections?
SQL Injection is a very old vulnerability – it was discovered in 1998. However, according to our 2020 research, 8 percent of websites and web applications have SQL Injection vulnerabilities.
Read our full report on the current state of web security.
How dangerous are SQL Injections?
A successful SQL Injection attack may lead to a complete compromise of a system or theft of the entire database. For example, an SQL Injection attack in 2019 led to the theft of complete tax data of 5 million people.
Read more about the most massive SQL Injection attack in 2019.
How to detect SQL Injections?
The only efficient way to detect SQL Injections is by using a vulnerability scanner, often called a DAST tool (dynamic application security testing). Acunetix is known to be top-of-the-line in detecting SQL Injections and other vulnerabilities. Acunetix is able to reach where other scanners fail.
Find out what Acunetix can do for you.
How to prevent SQL Injections?
The best way to prevent SQL Injections is to use safe programming functions that make SQL Injections impossible: parameterized queries (prepared statements) and stored procedures. Every major programming language currently has such safe functions and every developer should only use such safe functions to work with the database.
Browse a library of safe functions for all programming languages.
Từ khóa » Chống Sql Injection C#
-
Cách Chống Lỗi Sql Injection Trong C# | Nhận Viết ứng Dụng
-
Tìm Hiểu SQL Injection Và Cách Phòng Chống Trong ASP.NET
-
SQL Injection Là Gì? Cách Phòng Chống Tấn Công SQL Injection
-
SQL INJECTION VÀ CÁCH PHÒNG CHỐNG - Viblo
-
SQL Injection Và Cách Phòng Chống Trong ASP.NET
-
Hạn Chế Lỗi SQL Injection Cho Phần Mềm Quản Lý Quán Cafe Với C# ...
-
Anti SQL Injection Tool
-
How Can I Prevent SQL Injection In My Functions? [duplicate]
-
SQL Injection Tấn Công Và Cách Phòng Tránh - 123doc
-
SQL Injection Prevention - OWASP Cheat Sheet Series
-
Lỗi SQL Injection Và Cách Phòng Chống
-
SQL Injection Là Gì? Nguy Hiểm đến Mức Nào Và Làm Sao để Phòng ...
-
Preventing SQL Injection In C# Applications - Jonathan Crozier
-
SQL Injection And How To Prevent It? - Baeldung