How Do I Create A Guest VLAN Using The Web Interface On My ...
Maybe your like
In this article, dot1x is enabled on all the ports so that all the hosts that are authorized are assigned to VLAN 1. On ports 1/0/1 and 1/0/24, guest VLAN is enabled. If guests connect to the port, they are assigned to VLAN 2000, so that guests cannot access the internal VLAN, but can access each other in the guest VLAN.
- Create VLAN 2000.
- Select Switching > VLAN > Basic > VLAN Configuration. A screen similar to the following displays.
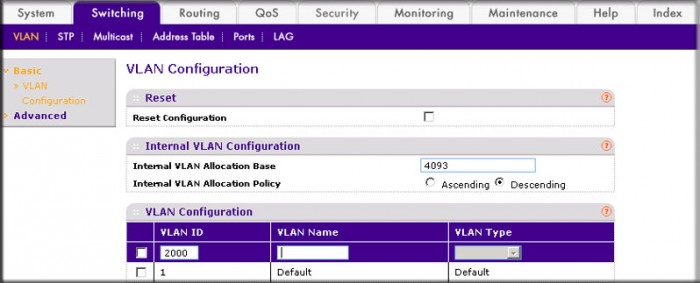
- In the VLAN ID field, enter 2000.
- In the VLAN Type field, select Static.
- Click Add.
- Select Switching > VLAN > Basic > VLAN Configuration. A screen similar to the following displays.
- Add ports to VLAN 2000.
- Select Switching > VLAN > Advanced > VLAN Membership. A screen similar to the following displays.
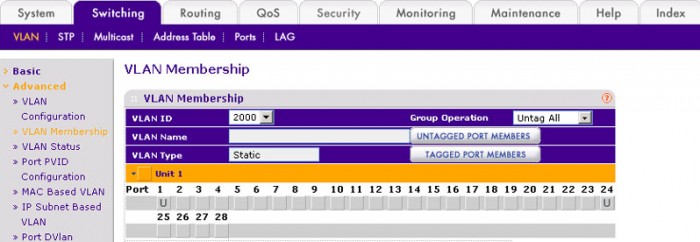
- In the VLAN ID list, select 2000 .
- Click Unit 1. The ports display.
- Click the gray boxes under ports 1 and 24 until U displays. The U specifies that the egress packet is untagged for the port.
- Click Apply.
- Select Switching > VLAN > Advanced > VLAN Membership. A screen similar to the following displays.
- Set force authorized mode on ports 1/0/6 and 1/0/12.
- Select Security > Port Authentication > Advanced > Port Authentication. A screen similar to the following displays.
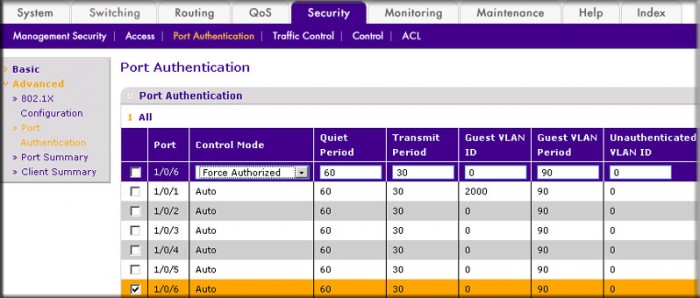
- Scroll down and select the Interface 1/0/6 and 1/0/12, check boxes.
- In the Control Mode list, select Force Authorized.
- Click Apply to save settings.
- Select Security > Port Authentication > Advanced > Port Authentication. A screen similar to the following displays.
- Enable dot1x on the switch. Make sure that 1/0/12 and 1/0/6 are configured as force authorized before you do this step; otherwise you cannot access the switch through the Web Interface.
- Select Security > Port Authentication > Basic > 802.1x Configuration. A screen similar to the following displays.
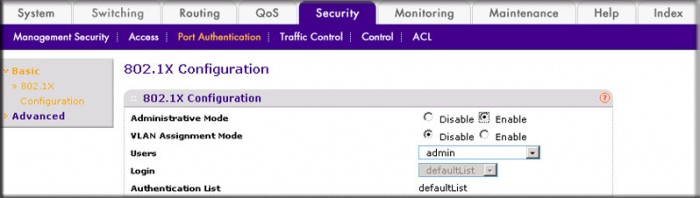
- For Administrative Mode, select the Enable radio button.
- Click Apply to save settings.
- Select Security > Port Authentication > Basic > 802.1x Configuration. A screen similar to the following displays.
- Configure the dot1x authentication list.
- Select Security > Management Security > Authentication List > Dot1x Authentication List. A screen similar to the following displays.
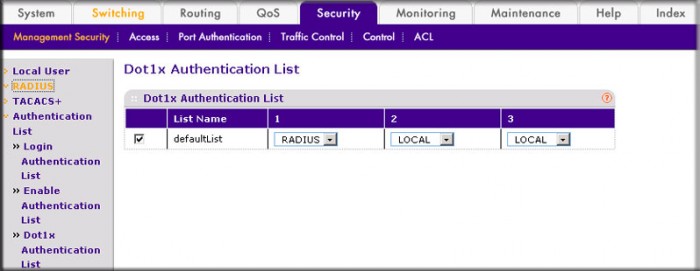
- Select the defaultList check box.
- In the 1 list, select RADIUS.
- Click Add.
- Select Security > Management Security > Authentication List > Dot1x Authentication List. A screen similar to the following displays.
- Configure the RADIUS authentication server.
- Select Security > Management Security > Radius > Server Configuration. A screen similar to the following displays.
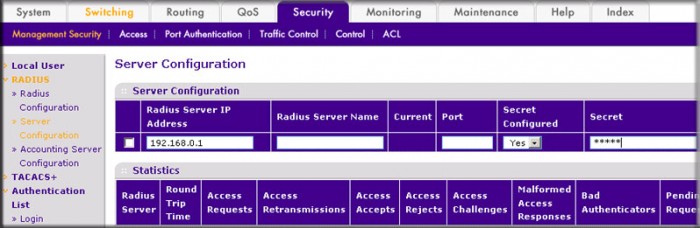
- In the Radius Server IP Address field, enter 192.168.0.1.
- In the Secret Configured field, select Yes.
- In the Secret field, enter 12345.
- Click Add.
- Select Security > Management Security > Radius > Server Configuration. A screen similar to the following displays.
- Configure the guest VLAN.
- Select Security > Port Authentication > Advanced > Port Authentication. A screen similar to the following displays.
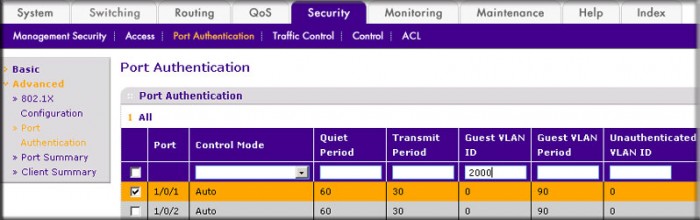
- Scroll down and select the port 1/0/1 and 1/0/24 check boxes.
- In the Guest VLAN ID field, enter 2000.
- Click Apply to save your settings.
- Select Security > Port Authentication > Advanced > Port Authentication. A screen similar to the following displays.
For more information, see the following support articles:
- What is the guest VLAN feature and how does it work with my managed switch?
- How do I create a guest VLAN using CLI commands on my managed switch?
This article applies to the following managed switches and their respective firmware:
- M5300 - firmware version 10.0.0.x
-
- M5300-28G (GSM7228S)
- M5300-5G (GSM7252S)
- M5300-28G3 (GSM7328Sv2h2)
- M5300-52G3 (GSM7352Sv2h2)
- M5300-28G_POE+ (GSM7228PSv1h2)
- M5300-52G-POE+ (GSM7252PSv1h2)
- M5300-28GF3 (GSM7328FSv2)
- M4100 - firmware version 10.0.1.x
-
- M4100-26G (GSM7224v2h2)
- M4100-50G (GSM7248v2h2)
- M4100-26G-POE (GSM7226Pv1h1)
- M4100-50G-POE+ (GSM7248Pv1h1)
- M4100-26G-POE (FSM7226Pv1h1)
- M4100-50-POE (FSM7250Pv1h1)
- M4100-D12G (GSM5212v1h1)
- M4100-D10-POE (FSM5210Pv1h1)
- M7100 - firmware version 10.0.1.x
-
- M7100-24X (XSM7224)
- XSM7224S - firmware version 9.0.1.x
Tag » How To Set Vlan On Switch Guest Wifi
-
AP Deployment With VLANs And Guest Network
-
How Set Up A VLAN For Guest Wi-Fi On A Managed Switch - WikiHow
-
Setting Up A VLAN For Guest Wifi - Spiceworks Community
-
Configuring Guest Wireless With VLANS - Expert Network Consultant
-
Guest WIFI Setup Into Separated VLAN? - Ubiquiti Community
-
Configuring Guest VLANs - Aruba Networks
-
Adding A Guest VLAN To A Network, Keeping Layers 2 And 3 Separate
-
How Do I Set Up A Guest VLAN On My Insight Managed Smart Cloud ...
-
How To Extend Guest Network When There Is A Switch Between Decos
-
Add A Separate Wireless Network For Guests - DrayTek
-
How To Create A Guest Network VLAN Without Allowing Access To LAN ...
-
Configuring A VLAN On The Linksys Managed Switch
-
VLANS On Home Networks- Setup And Use
-
Solved: Creating VLAN For Guests - Cisco Community